Why you need Azure Conditional Access Policies
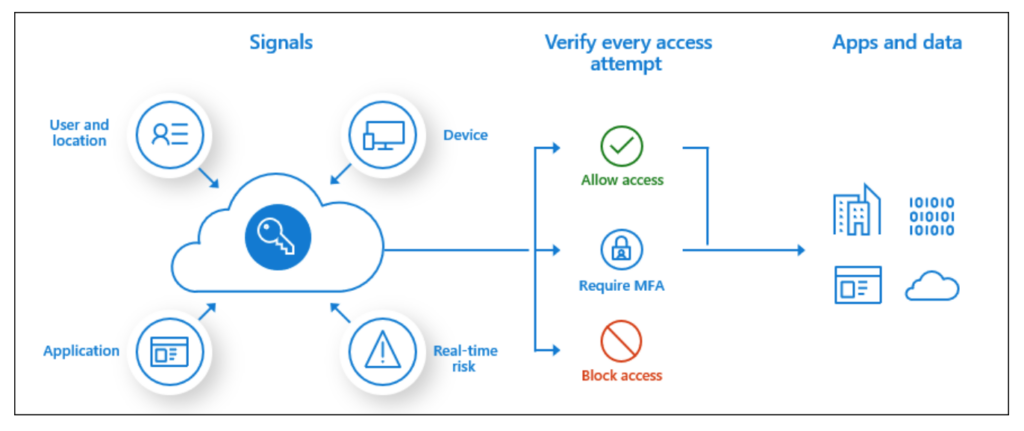
Overview
Having undertaken a number of Red Team assessments over the last 5 years, one of the common things that is uncovered during these assessments is the lack of robust Microsoft Azure AD conditional access policies.
Microsoft Azure AD Conditional access is a premium feature and disabled by default. To enable it you need a P1, P2 or Trial License. Once turned on everything is allowed by default. There is a feature called security defaults that applies when no policies are created but once you create a policy then anything that is not explicitly blocked is effectively allowed!
Attack Scenario
As an example organisations often setup MFA but then forget to implement unwanted scenarios with a block policy. Things such as geo fencing or detecting if the device connecting is approved by the organisation. In this scenario this leaves the door wide open for a hacker who has compromised a user account to potentially gain access to the organisations sensitive resources.
Best Practices
The following are a list of common best practices that every organisation should consider when implementing Microsoft Azure AD Conditional Access Policies:
- Apply Conditional Access to every authentication request for all users and applications.
- Minimise the number of policies.
- Use a standard naming convention.
- Plan for some disruption for newly created policies.
- Scope new policies to test accounts and run through a test plan to validate expected results.
- Configure Report Only mode when defining new policies.
- Use emergency access accounts in exclusions.
- Block legacy authentication while implementing MFA policies.
- Use the What If tool for use case testing or troubleshooting an issue.
- Be aware that some apps have multiple child apps such as Office 365.
- Consider Guest Access when defining policies.
- Block countries from which you never expect a sign in using Geofencing.
Summary
As a defender make sure you are monitoring all of your Azure AD sign-ins. Use a good SIEM solution like Elastic to capture these events and if your budget can afford it ensure you are collecting these events for more than 90 days. Lastly make sure you include testing of these policies in any Penetration testing or Red Team engagements you undertake.