Posts by External News-Site
New SLAP & FLOP Attacks Expose Apple M-Series Chips to Speculative Execution Exploits
A team of security researchers from Georgia Institute of Technology and Ruhr University Bochum has demonstrated two new side-channel attacks targeting Apple silicon that could be exploited to leak sensitive information from web browsers like Safari and Google Chrome.
The attacks have been codenamed Data Speculation Attacks via Load Address Prediction on Apple Silicon (SLAP) and Breaking the
Phone Phishing Gang Busted: Eight Arrested in Belgium and Netherlands
Belgian and Dutch authorities have arrested eight suspects in connection with a “phone phishing” gang that primarily operated out of the Netherlands with an aim to steal victims’ financial data and funds.
As part of the international operation, law enforcement agencies carried out 17 searches in different locations in Belgium and the Netherlands, Europol said. In addition, large amounts of cash,
Ransomware attack hits leading heart surgery device maker
Artivion, a leading manufacturer of heart surgery medical devices, has disclosed a November 21 ransomware attack that disrupted its operations and forced it to take some systems offline. […]
Read MoreMicrosoft NTLM Zero-Day to Remain Unpatched Until April
The second zero-day vulnerability found in Windows NTLM in the past two months paves the way for relay attacks and credential theft. Microsoft has no patch, but released updated NTLM cyberattack mitigation advice.
Read MoreBlack Basta Ransomware Evolves with Email Bombing, QR Codes, and Social Engineering
The threat actors linked to the Black Basta ransomware have been observed switching up their social engineering tactics, distributing a different set of payloads such as Zbot and DarkGate since early October 2024.
“Users within the target environment will be email bombed by the threat actor, which is often achieved by signing up the user’s email to numerous mailing lists simultaneously,” Rapid7
Researchers Uncover Prompt Injection Vulnerabilities in DeepSeek and Claude AI
Details have emerged about a now-patched security flaw in the DeepSeek artificial intelligence (AI) chatbot that, if successfully exploited, could permit a bad actor to take control of a victim’s account by means of a prompt injection attack.
Security researcher Johann Rehberger, who has chronicled many a prompt injection attack targeting various AI tools, found that providing the input “Print
Blue Yonder SaaS giant breached by Termite ransomware gang
The Termite ransomware gang has officially claimed responsibility for the November breach of software as a service (SaaS) provider Blue Yonder. […]
Read MoreEU enacts new laws to strengthen cybersecurity defenses and coordination
The European Union has enacted two new laws to bolster its cybersecurity defenses and coordination mechanisms.
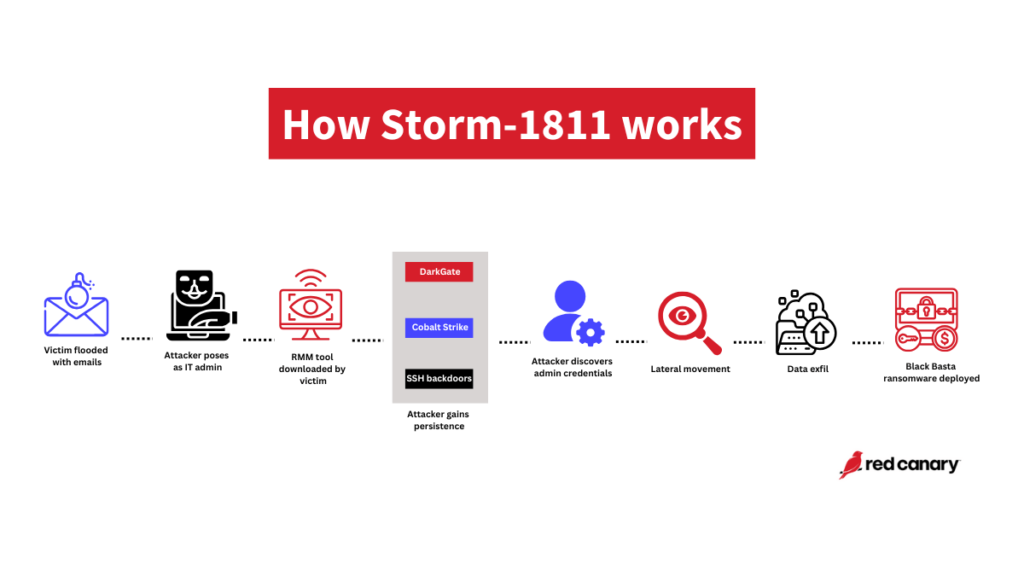
Read MoreStorm-1811 exploits RMM tools to drop Black Basta ransomware
Storm-1811’s latest help desk scam begins with email bombing leading to IT impersonation and ends with Black Basta ransomware
Read MoreInterpol Cyber-Fraud Action Nets More Than 5K Arrests
Chalk up another win for global cooperation among law enforcement, this time targeting seven types of cyber fraud, including voice phishing and business email compromise.
Read More