
Data Security and Data Privacy
Being proactive and prepared is an essential approach to safeguarding your data. Not knowing where your data resides or who has access to it is no longer an excuse.
Our data security, data privacy, and governance services help you to solve your most important data risk concerns.
Our Core Focus Areas
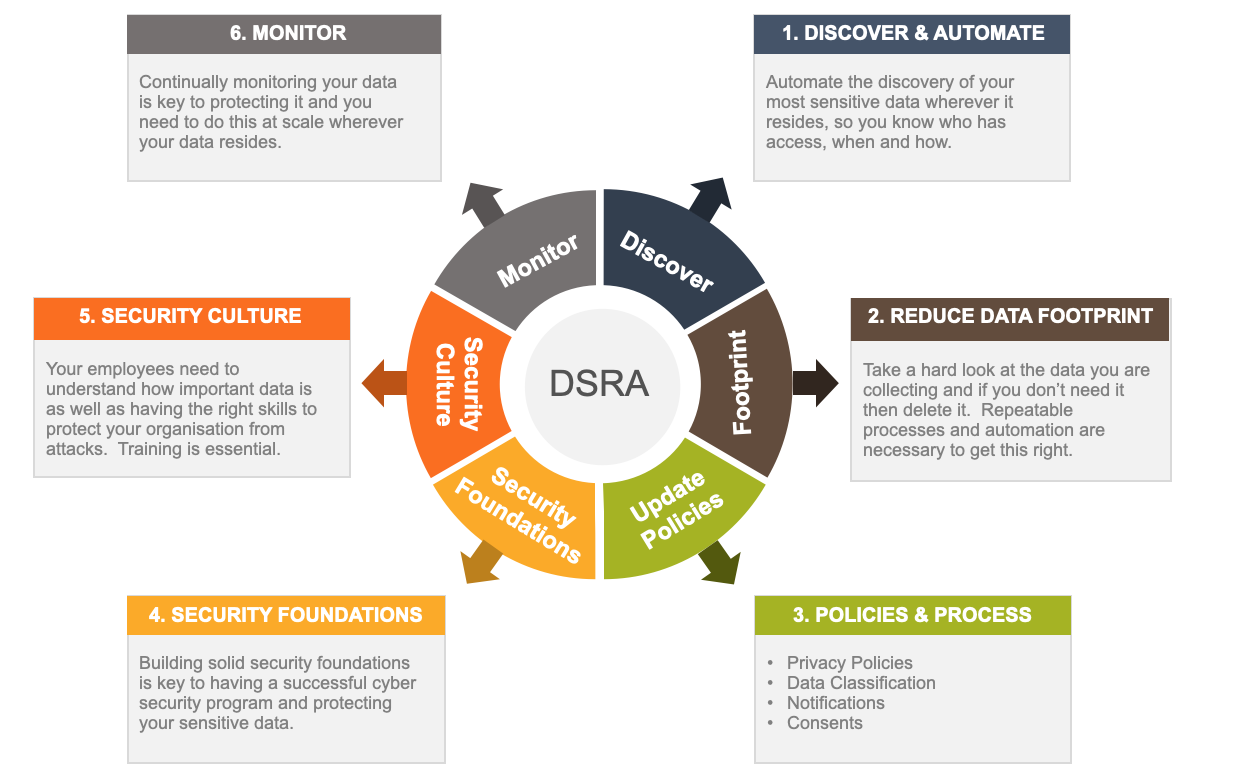
Our data security posture management service provides the following five core capabilities:
- Data discovery - Automatically find and classify sensitive, regulated, critical, and dark data. Uncover shadow data and build a dynamic inventory for all your data everywhere.
- Creating a data map and mapping user access to data - Track who has access to sensitive data, and automatically generate a map of user access. Reduce permissions to least privilege and eliminate overprivileged access issues.
- Tracking data flows and connections across and outside the organisation - cross-border transfers, data residency, monitor data processing & sharing, secrets in dev data.
- Protecting against data exposure - Automate and orchestrate remediation for high-risk data with trigger alerts and workflows based on activity. Remediate data security issues by enforcing controls over your sensitive data.
- Assess and report on data security posture - Get in-depth reporting on potential data risks, policy violations, and data security vulnerabilities easily. Monitor your data through assessment scores and reports to protect against unauthorized exposure.
Benefits
Join over 2500+ people who receive our cyber security tips and news every 2 weeks
*Data Privacy
