Cyber Security
Five Eyes Agencies Expose APT29’s Evolving Cloud Attack Tactics
Cybersecurity and intelligence agencies from the Five Eyes nations have released a joint advisory detailing the evolving tactics of the Russian state-sponsored threat actor known as APT29.
The hacking outfit, also known as BlueBravo, Cloaked Ursa, Cozy Bear, Midnight Blizzard (formerly Nobelium), and The Dukes, is assessed to be affiliated with the Foreign Intelligence Service (SVR) of the
New Hugging Face Vulnerability Exposes AI Models to Supply Chain Attacks
Cybersecurity researchers have found that it’s possible to compromise the Hugging Face Safetensors conversion service to ultimately hijack the models submitted by users and result in supply chain attacks.
“It’s possible to send malicious pull requests with attacker-controlled data from the Hugging Face service to any repository on the platform, as well as hijack any models that are submitted
New IDAT loader version uses steganography to push Remcos RAT
A hacking group tracked as ‘UAC-0184’ was observed utilizing steganographic image files to deliver the Remcos remote access trojan (RAT) onto the systems of a Ukrainian entity operating in Finland. […]
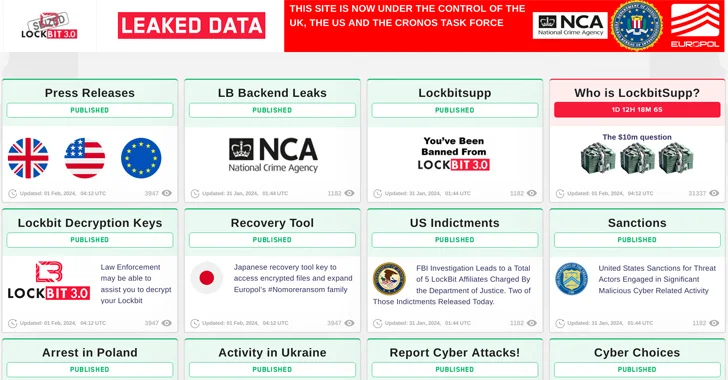
Read MoreLockBit’s Leak Site Reemerges, a Week After ‘Complete Compromise’
Is LockBit dead? Law enforcement and the group itself seem to be telling conflicting stories.
Read MoreHijacked subdomains of major brands used in massive spam campaign
A massive ad fraud campaign named “SubdoMailing” is using over 8,000 legitimate internet domains and 13,000 subdomains to send up to five million emails per day to generate revenue through scams and malvertising. […]
Read MoreNorth Korean Hackers Targeting Developers with Malicious npm Packages
A set of fake npm packages discovered on the Node.js repository has been found to share ties with North Korean state-sponsored actors, new findings from Phylum show.
The packages are named execution-time-async, data-time-utils, login-time-utils, mongodb-connection-utils, and mongodb-execution-utils.
One of the packages in question, execution-time-async, masquerades as its legitimate
U.S. Offers $15 Million Bounty to Hunt Down LockBit Ransomware Leaders
The U.S. State Department has announced monetary rewards of up to $15 million for information that could lead to the identification of key leaders within the LockBit ransomware group and the arrest of any individual participating in the operation.
“Since January 2020, LockBit actors have executed over 2,000 attacks against victims in the United States, and around the world, causing costly
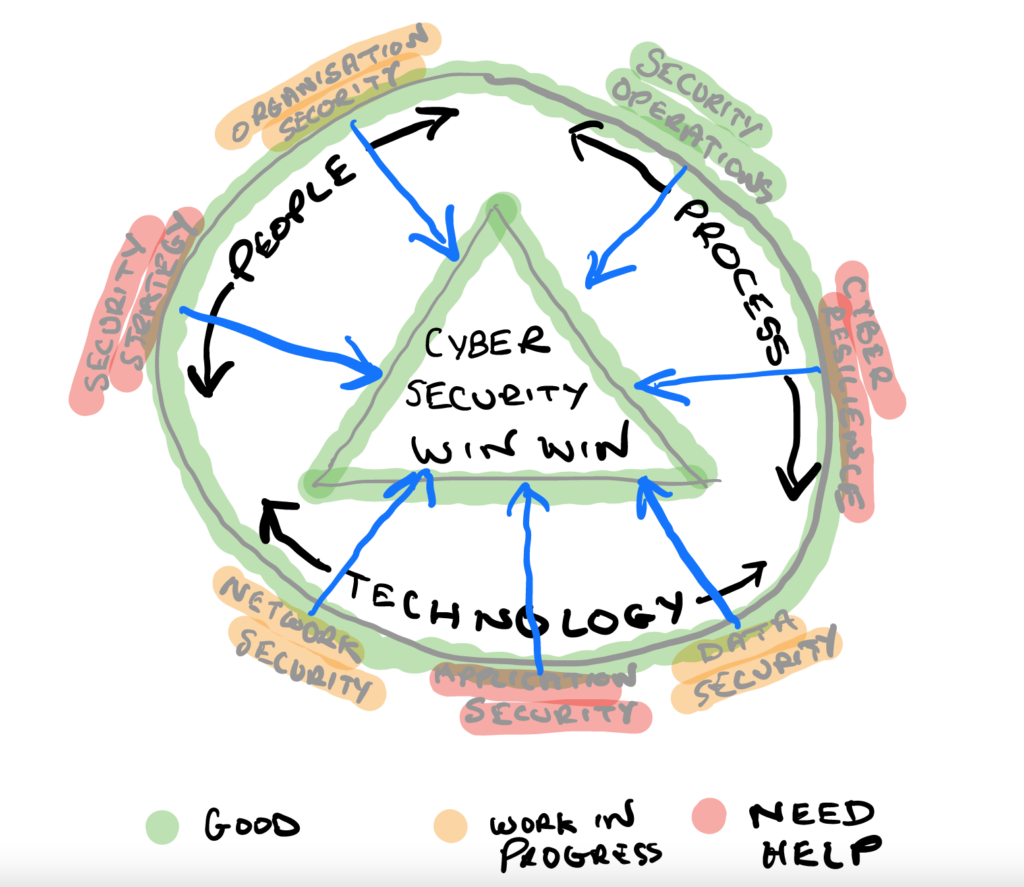
How to build and maintain a successful cybersecurity program
In this article I’m going to be talking about how to build a successful cybersecurity program. This unique strategy is something I’ve learned and put into action over the last 30 years and that has helped to keep organisations safe, build resilience and maintain a continuous improvement plan that provides a WIN WIN for cybersecurity…
Read MorePolice arrests LockBit ransomware members, release decryptor in global crackdown
Law enforcement arrested two operators of the LockBit ransomware gang in Poland and Ukraine, created a decryption tool to recover encrypted files for free, and seized over 200 crypto-wallets after hacking the cybercrime gang’s servers in an international crackdown operation. […]
Read MoreNew Report Reveals North Korean Hackers Targeting Defense Firms Worldwide
The North Korean state-sponsored threat actors have been attributed to a cyber espionage campaign targeting the defense sector across the world.
In a joint advisory published by Germany’s Federal Office for the Protection of the Constitution (BfV) and South Korea’s National Intelligence Service (NIS), the agencies said the goal of the attacks is to plunder advanced defense technologies in a “