Security Program
Virtual CISO for hire: Build cyber security resilience
As cybersecurity threats continue to evolve and become more sophisticated, organizations must stay one step ahead to protect their valuable data and assets. In today’s digital landscape, the role of a Chief Information Security Officer (CISO) is vital in ensuring the security of an organisation’s systems and information. However, not every organisation has the resources…
Read MoreMoroccan Cybercrime Group Steals Up to $100K Daily Through Gift Card Fraud
Microsoft is calling attention to a Morocco-based cybercrime group dubbed Storm-0539 that’s behind gift card fraud and theft through highly sophisticated email and SMS phishing attacks.
“Their primary motivation is to steal gift cards and profit by selling them online at a discounted rate,” the company said in its latest Cyber Signals report. “We’ve seen some examples where
To be or not to be a CISO
Do you aspire to be a CISO? As a former CISO, I felt compelled to write this article after seeing many articles about the role of a CISO and opinions on how hard it is becoming. I’m uncertain whether many people today would actually aspire to be a CISO given the pressures, the demands of…
Read More30 years of the CISO role – how things have changed since Steve Katz
The first-ever CISO was mostly a technically oriented executive. They’ve since evolved into masters of risk management, threat mitigation, regulatory compliance, data privacy, and much more.
When Steve Katz became the first-ever CISO in 1995, Netscape Navigator was the world’s most popular browser, Mark Zuckerberg was in middle school, smartphones were a decade away, and SSL 2.0 was brand new.
Read MoreHow to build and maintain a successful cybersecurity program
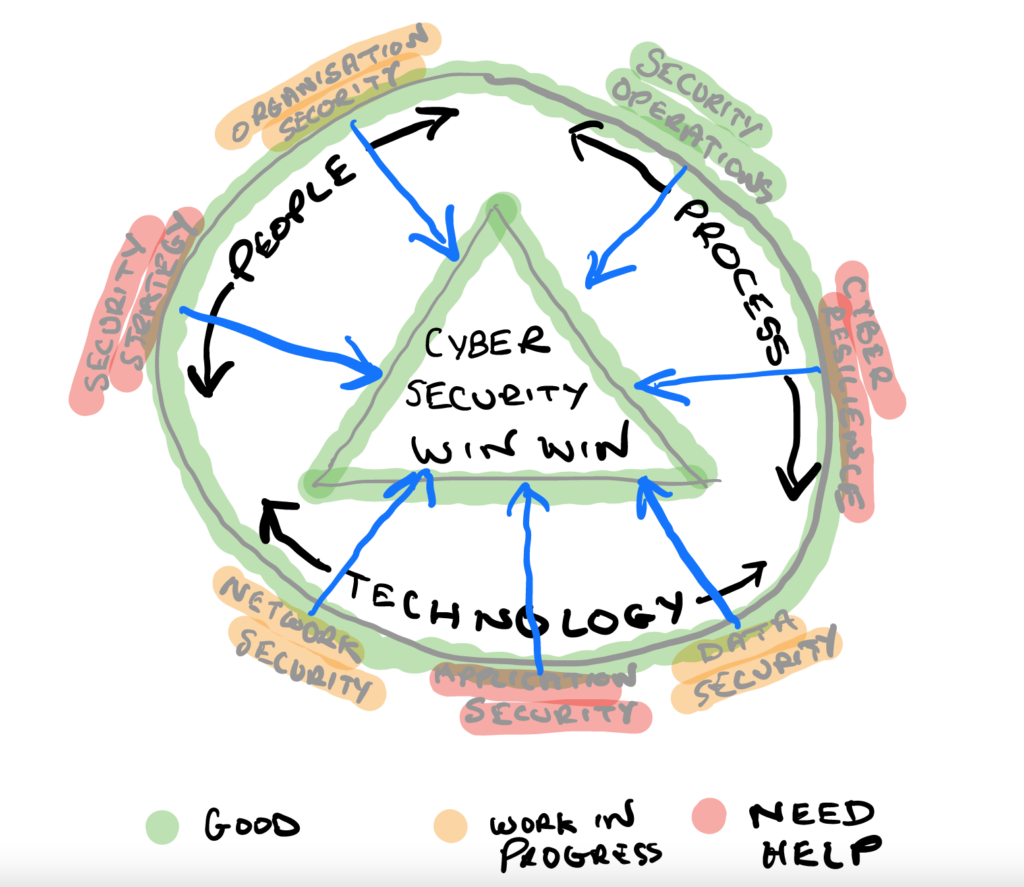
In this article I’m going to be talking about how to build a successful cybersecurity program. This unique strategy is something I’ve learned and put into action over the last 30 years and that has helped to keep organisations safe, build resilience and maintain a continuous improvement plan that provides a WIN WIN for cybersecurity…
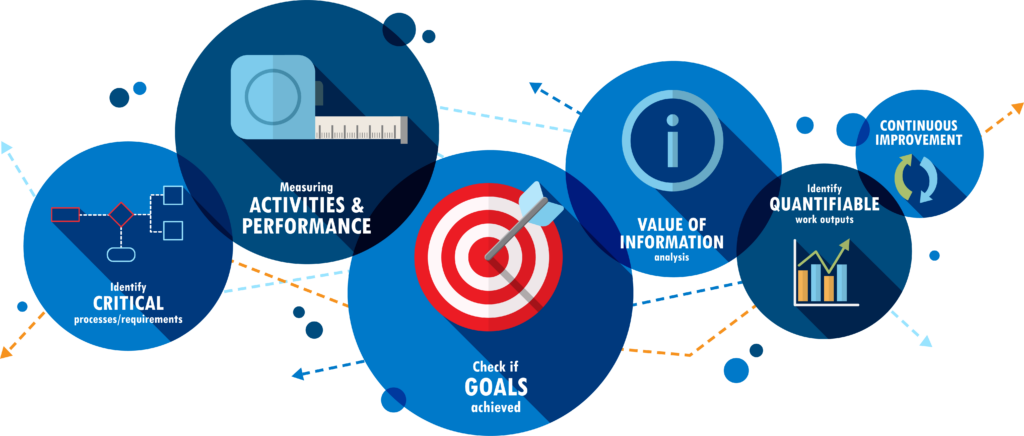
Read MoreHow to measure the success of your cybersecurity program
Being asked to present to the board and other key stakeholders in your business about the state of your cybersecurity program can be a daunting prospect.
Putting aside the technical jargon can also be challenging for even the most seasoned security professional.
Read MoreMost Sophisticated iPhone Hack Ever Exploited Apple’s Hidden Hardware Feature
The Operation Triangulation spyware attacks targeting Apple iOS devices leveraged never-before-seen exploits that made it possible to even bypass pivotal hardware-based security protections erected by the company.
Russian cybersecurity firm Kaspersky, which discovered the campaign at the beginning of 2023 after becoming one of the targets, described it as
Lockbit ransomware disrupts emergency care at German hospitals
German hospital network Katholische Hospitalvereinigung Ostwestfalen (KHO) has confirmed that recent service disruptions were caused by a Lockbit ransomware attack where the threat actors gained access to IT systems and encrypted devices on the network. […]
Read More