How-To
How to build a successful cybersecurity program
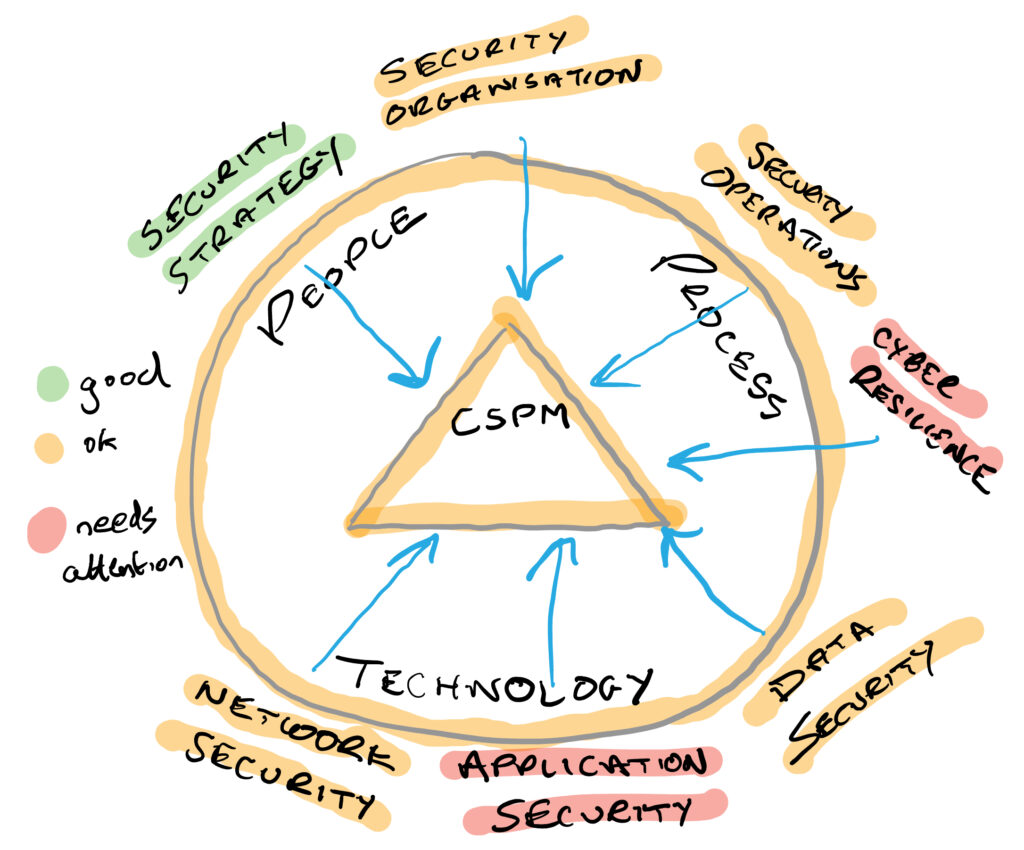
In this video I will be taking you through a cybersecurity framework that I have developed and perfected over the last 25 years to help organisations build strong cybersecurity programs, reduce risk and remain safe. Ready to find out more? Book in a Call
Read MoreData Security and Privacy: Time to act is now!
With the latest Data Privacy law reforms on the horizon and having just finished off Privacy Awareness Week, #PAW2024, in Australia this article is aimed at all organisations that hold sensitive data. Data breaches are nasty, and they impact everyone involved. Australia has seen some of the largest data breaches over the last 18 months.…
Read MoreTo be or not to be a CISO
Do you aspire to be a CISO? As a former CISO, I felt compelled to write this article after seeing many articles about the role of a CISO and opinions on how hard it is becoming. I’m uncertain whether many people today would actually aspire to be a CISO given the pressures, the demands of…
Read MoreHow To: Email Phishing, malicious payload analysis walkthrough
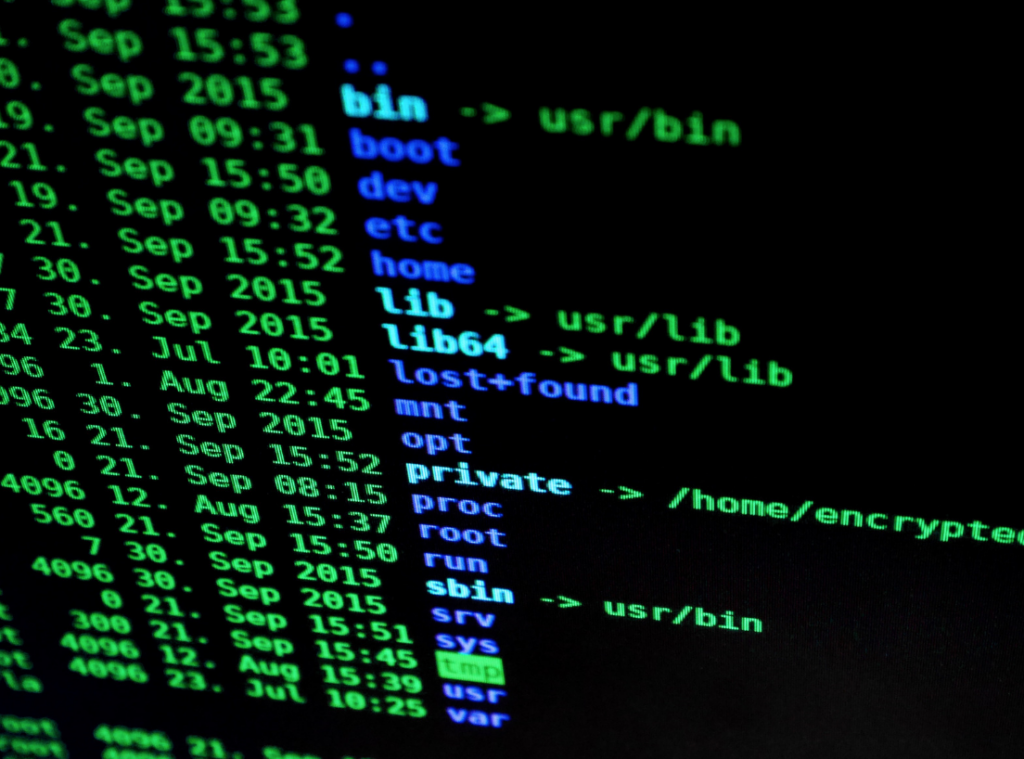
The other day I received a malicious phishing email with what appeared to be an invoice but in fact was a javascript embedded in an HTML document. So let’s get into it. Initial Inspection When I initially opened the document in my visual code editor it appeared as follows: The second line declares a variable…
Read MoreData Security in the era of AI
In the era of AI, forward-thinking organisations need to adopt a new approach to protecting their most sensitive data.
The growing volume of data and the propensity of its use means that organisations can no longer rely on traditional and manual data processing methods to manage unstructured data. The only way to manage data in the future will be with automation, and ironically AI.
Read MoreCyberChef : how to decode your data the easy way
Intro If you haven’t heard of CyberChef you may be thinking that it is a new robot being created to compete on the next series of “My Kitchen Rules” or go head to head with Gordon Ramsay on “Kitchen Nightmares”! Actually CyberChef or at least the one I’m referring to is actually a really cool…
Read MoreHow to measure the success of your cybersecurity program
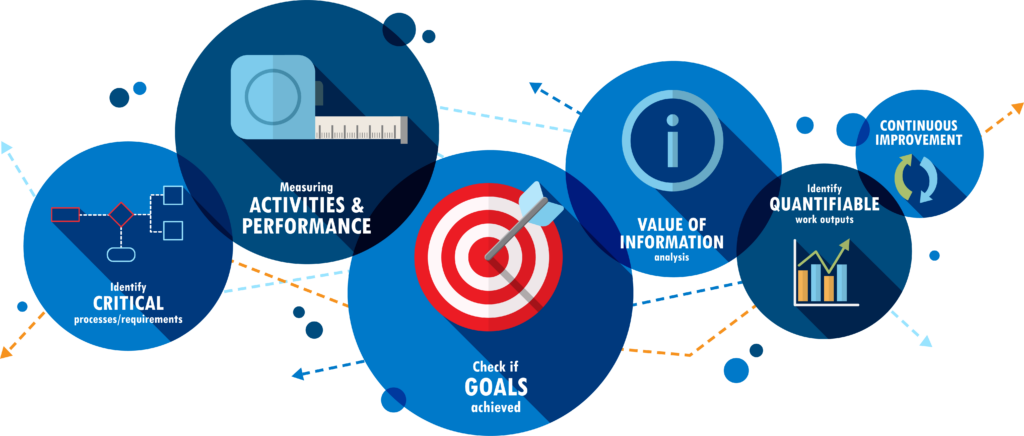
Being asked to present to the board and other key stakeholders in your business about the state of your cybersecurity program can be a daunting prospect.
Putting aside the technical jargon can also be challenging for even the most seasoned security professional.
Read MoreRansomware Resilience: How to prepare and respond in a crisis
Are you prepared for a ransomware attack? What should you do if you become a victim? This guide provides some practical advice you need to know & do to survive.
Read MoreTime altering techniques to evade your security controls
In this article I’ll be talking about ‘Time Travel’ and sadly it’s not an episode of ‘Dr Who’ or ‘Back to the Future’ and not really ‘Time Travel’ but I needed a catchy title! So what I am referring to is how hackers often change the system time of a particular system they are exploiting…
Read MoreEndpoint Security Part 5: How to setup an automated isolation workflow when malware is detected
In this continuing series on endpoint security protections I’ll be showing you how to fully automate host isolation using ‘Tines’ and ‘Elastic’. This article assumes you are familiar with using Elastic SIEM and have some exposure to Tines. Tines is a smart automation workflow solution that I came across last year. What I like about…
Read More