How-To
Endpoint Security Part 4: How to create a playbook to isolate a machine and alert your SOC team
Overview In this fourth article of a 5 part series on ‘Endpoint Security’ I’m going to be showing you how to create a rule in your Elastic SIEM to generate an alert and isolate a host if the presence of malware is detected. Step One – Create the detection rule In your Kibana console select:…
Read MoreEndpoint Security Part 3: How to correlate threat intelligence
Overview In this third article of a 5 part series on ‘Endpoint Security’ I’m going to be showing you how you can incorporate ‘Threat Intelligence’ into your security operations strategy. There has been a lot written about threat intelligence over the last decade and it has different meanings to people depending on what industry you…
Read MoreEndpoint Security Part 2: Enriching your security event data
In this second part series on ‘Endpoint Security’ I’m going to delve into how you can enrich your security event data to provide further context to assist your security analysts when investigating incidents. In this example we will lead off where we ended from ‘Endpoint Security Part 1’ and so if you were following the…
Read MoreEndpoint Security Part1: Collecting the essential security events for your windows systems
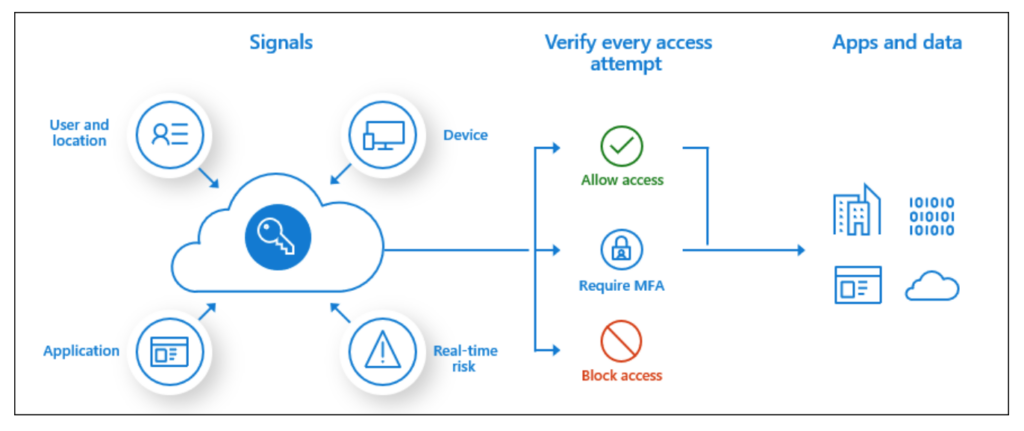
Why you need Azure Conditional Access Policies
Overview Having undertaken a number of Red Team assessments over the last 5 years, one of the common things that is uncovered during these assessments is the lack of robust Microsoft Azure AD conditional access policies. Microsoft Azure AD Conditional access is a premium feature and disabled by default. To enable it you need a…
Read MoreKeeping your service provider honest!
We all expect our service providers to do the right thing, abide by contractural terms, provide support when they are meant to and be available when in need. However, sometimes that doesn’t always happen and so how do you keep your provider on the hook if things do go awry? In this example I’ll look…
Read MoreExport your passwords from LastPass
Unless you have been living under a rock for the last few months you will know that LastPass has suffered a major breach. If like me you feel you can no longer trust LastPass to safeguard your crown jewels then this article explains how to: Export your passwords from LastPass Delete and permanently erase all…
Read More