Security News
Incognito Darknet Market Mass-Extorts Buyers, Sellers
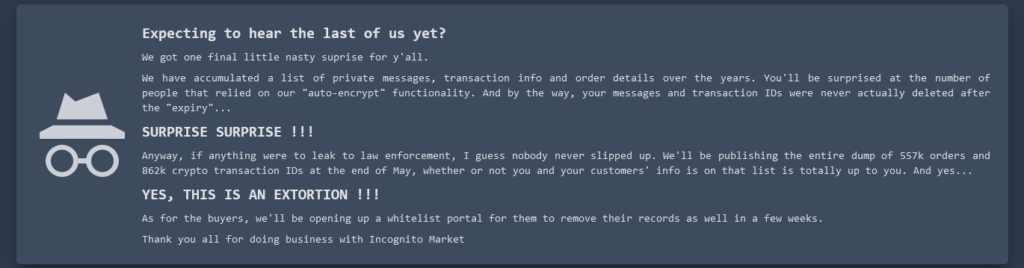
Borrowing from the playbook of ransomware purveyors, the darknet narcotics bazaar Incognito Market has begun extorting all of its vendors and buyers, threatening to publish cryptocurrency transaction and chat records of users who refuse to pay a fee ranging from $100 to $20,000. The bold mass extortion attempt comes just days after Incognito Market administrators reportedly pulled an “exit scam” that left users unable to withdraw millions of dollars worth of funds from the platform.
Read MoreMicrosoft Confirms Russian Hackers Stole Source Code, Some Customer Secrets
Microsoft on Friday revealed that the Kremlin-backed threat actor known as Midnight Blizzard (aka APT29 or Cozy Bear) managed to gain access to some of its source code repositories and internal systems following a hack that came to light in January 2024.
“In recent weeks, we have seen evidence that Midnight Blizzard is using information initially exfiltrated from our
Google Engineer Steals AI Trade Secrets for Chinese Companies
Chinese national Linwei Ding is accused of pilfering more than 500 files containing Google IP while affiliating with two China-based startups at the same time.
Read MoreCritical Fortinet flaw may impact 150,000 exposed devices
Scans on the public web show that approximately 150,000 Fortinet FortiOS and FortiProxy secure web gateway systems are vulnerable to CVE-2024-21762, a critical security issue that allows executing code without authentication. […]
Read MoreNSA’s Zero-Trust Guidelines Focus on Segmentation
Zero-trust architectures are essential protective measures for the modern enterprise. The latest NSA guidance provides detailed recommendations on how to implement the networking angle of the concept.
Read MoreCisco Issues Patch for High-Severity VPN Hijacking Bug in Secure Client
Cisco has released patches to address a high-severity security flaw impacting its Secure Client software that could be exploited by a threat actor to open a VPN session with that of a targeted user.
The networking equipment company described the vulnerability, tracked as CVE-2024-20337 (CVSS score: 8.2), as allowing an unauthenticated, remote attacker to conduct a carriage return line feed (CRLF
Hackers target Docker, Hadoop, Redis, Confluence with new Golang malware
Hackers are targeting misconfigured servers running Apache Hadoop YARN, Docker, Confluence, or Redis with new Golang-based malware that automates the discovery and compromise of the hosts. […]
Read MoreU.S. Cracks Down on Predatory Spyware Firm for Targeting Officials and Journalists
The U.S. Department of Treasury’s Office of Foreign Assets Control (OFAC) sanctioned two individuals and five entities associated with the Intellexa Alliance for their role in “developing, operating, and distributing” commercial spyware designed to target government officials, journalists, and policy experts in the country.
“The proliferation of commercial spyware poses distinct and growing
Alert: GhostSec and Stormous Launch Joint Ransomware Attacks in Over 15 Countries
The cybercrime group called GhostSec has been linked to a Golang variant of a ransomware family called GhostLocker.
“TheGhostSec and Stormous ransomware groups are jointly conducting double extortion ransomware attacks on various business verticals in multiple countries,” Cisco Talos researcher Chetan Raghuprasad said in a report shared with The Hacker News.
“GhostLocker and
BlackCat Ransomware Group Implodes After Apparent $22M Payment by Change Healthcare
There are indications that U.S. healthcare giant Change Healthcare has made a $22 million extortion payment to the infamous BlackCat ransomware group (a.k.a. “ALPHV“) as the company struggles to bring services back online amid a cyberattack that has disrupted prescription drug services nationwide for weeks.
Read More