New Malware Hits 300,000 Users with Rogue Chrome and Edge Extensions

Originally Published at The Hacker News by External News-Site
An ongoing, widespread malware campaign has been observed installing rogue Google Chrome and Microsoft Edge extensions via a trojan distributed via fake websites masquerading as popular software.
"The trojan malware contains different deliverables ranging from simple adware extensions that hijack searches to more sophisticated malicious scripts that deliver local extensions to steal private data and execute various commands," the ReasonLabs research team said in an analysis.
"This trojan malware, existing since 2021, originates from imitations of download websites with add-ons to online games and videos."
The malware and the extensions have a combined reach of at least 300,000 users of Google Chrome and Microsoft Edge, indicating that the activity has a broad impact.
At the heart of the campaign is the use of malvertising to push lookalike websites promoting known software like Roblox FPS Unlocker, YouTube, VLC media player, Steam, or KeePass to trick users searching for these programs into downloading a trojan, which serves as a conduit for installing the browser extensions.
The digitally signed malicious installers register a scheduled task that, in turn, is configured to execute a PowerShell script responsible for downloading and executing the next-stage payload fetched from a remote server.
This includes modifying the Windows Registry to force the installation of extensions from Chrome Web Store and Microsoft Edge Add-ons that are capable of hijacking search queries on Google and Microsoft Bing and redirecting them through attacker-controlled servers.
"The extension cannot be disabled by the user, even with Developer Mode 'ON,'" ReasonLabs said. "Newer versions of the script remove browser updates."
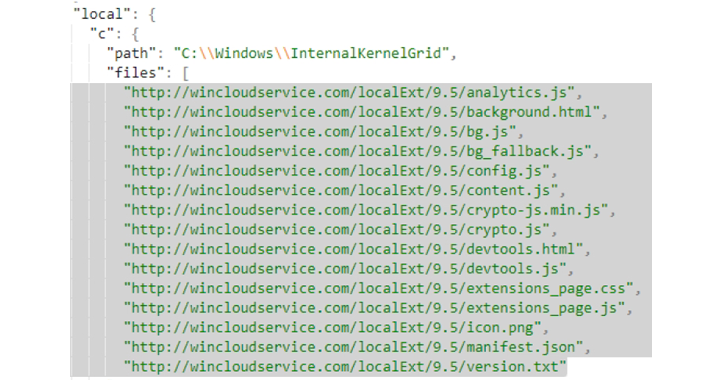
It also launches a local extension that is downloaded directly from a command-and-control (C2) server, and comes with extensive capabilities to intercept all web requests and send them to the server, receive commands and encrypted scripts, and inject and load scripts into all pages.
On top of that, it hijacks search queries from Ask.com, Bing, and Google, and funnels them through its servers and then on to other search engines.
Users who are affected the malware attack are recommended to delete the scheduled task that reactivates the malware each day, remove the Registry keys, and delete the below files and folders from the system -
- C:Windowssystem32Privacyblockerwindows.ps1
- C:Windowssystem32Windowsupdater1.ps1
- C:Windowssystem32WindowsUpdater1Script.ps1
- C:Windowssystem32Optimizerwindows.ps1
- C:Windowssystem32Printworkflowservice.ps1
- C:Windowssystem32NvWinSearchOptimizer.ps1 - 2024 version
- C:Windowssystem32kondserp_optimizer.ps1 - May 2024 version
- C:WindowsInternalKernelGrid
- C:WindowsInternalKernelGrid3
- C:WindowsInternalKernelGrid4
- C:WindowsShellServiceLog
- C:windowsprivacyprotectorlog
- C:WindowsNvOptimizerLog
This is not the first time similar campaigns have been observed in the wild. In December 2023, the cybersecurity company detailed another trojan installer delivered through torrents that installed malicious web extensions masquerading as VPN apps but are actually designed to run a "cashback activity hack."
Source URL: https://thehackernews.com/2024/08/new-malware-hits-300000-users-with.html
Author: External News-Site