Background
Among today's most dangerous cyber threats, few ransomware groups have demonstrated the level of sophistication and business acumen exhibited by Qilin (also known as Agenda). This Russian-speaking ransomware-as-a-service (RaaS) operation has distinguished itself not just through technical prowess, but through an almost corporate-like approach to criminal enterprise that includes offering legal counsel to affiliates a disturbing evolution that signals the maturation of ransomware operations into full-fledged criminal businesses.
The Qilin Criminal Enterprise
First emerging in late 2022, Qilin quickly established itself as a formidable player in the ransomware ecosystem. What sets this group apart isn't just their technical capabilities, but their structured approach to criminal operations. Operating under a RaaS model, Qilin provides the infrastructure, tools, and support that enable affiliates to conduct attacks while taking a percentage of ransom payments essentially functioning as a criminal franchise operation.
The group's name, derived from a mythical Chinese creature, reflects their ambition to be seen as legendary in the cybercriminal underground. Unfortunately, their reputation is well-earned through a series of high-profile attacks that have crippled organisations worldwide.
Tactics, Techniques, and Procedures: A Technical Deep Dive
Initial Access and Persistence
Qilin affiliates typically gain initial access through several vectors:
Vulnerable Remote Services: The group aggressively targets exposed Remote Desktop Protocol (RDP) services, VPN appliances, and other remote access solutions. They exploit both known vulnerabilities and weak authentication mechanisms to establish their initial foothold.
Phishing Campaigns: Sophisticated spear-phishing emails containing malicious attachments or links serve as another primary infection vector. These campaigns often target specific individuals within organizations, demonstrating significant reconnaissance efforts.
Supply Chain Compromises: In more advanced operations, Qilin has demonstrated the ability to compromise managed service providers (MSPs) and use these trusted relationships to access multiple client networks simultaneously.
Lateral Movement and Reconnaissance
Once inside a network, Qilin operators employ a methodical approach to expansion:
Living-off-the-Land Techniques: The group extensively uses legitimate administrative tools like PowerShell, Windows Management Instrumentation (WMI), and PsExec to move laterally through networks, making detection significantly more challenging.
Active Directory Exploitation: Qilin demonstrates sophisticated understanding of Windows environments, often compromising domain controllers to gain enterprise-wide access and deploy ransomware across entire networks simultaneously.
Data Discovery and Exfiltration: Before encryption, operators conduct thorough reconnaissance to identify and exfiltrate valuable data. This reconnaissance phase can last weeks or months, during which time sensitive information is systematically stolen.
The Encryption Phase
Qilin's ransomware payload is particularly destructive:
Multi-Platform Capability: The group develops variants targeting Windows, Linux, and VMware ESXi environments, ensuring comprehensive coverage of enterprise infrastructure.
Selective Encryption: Rather than encrypting every file, Qilin employs selective encryption techniques that maximize damage while minimizing encryption time, reducing the window for detection and response.
Anti-Analysis Features: The malware incorporates multiple techniques to evade detection and analysis, including code obfuscation, anti-debugging measures, and the ability to terminate security processes.
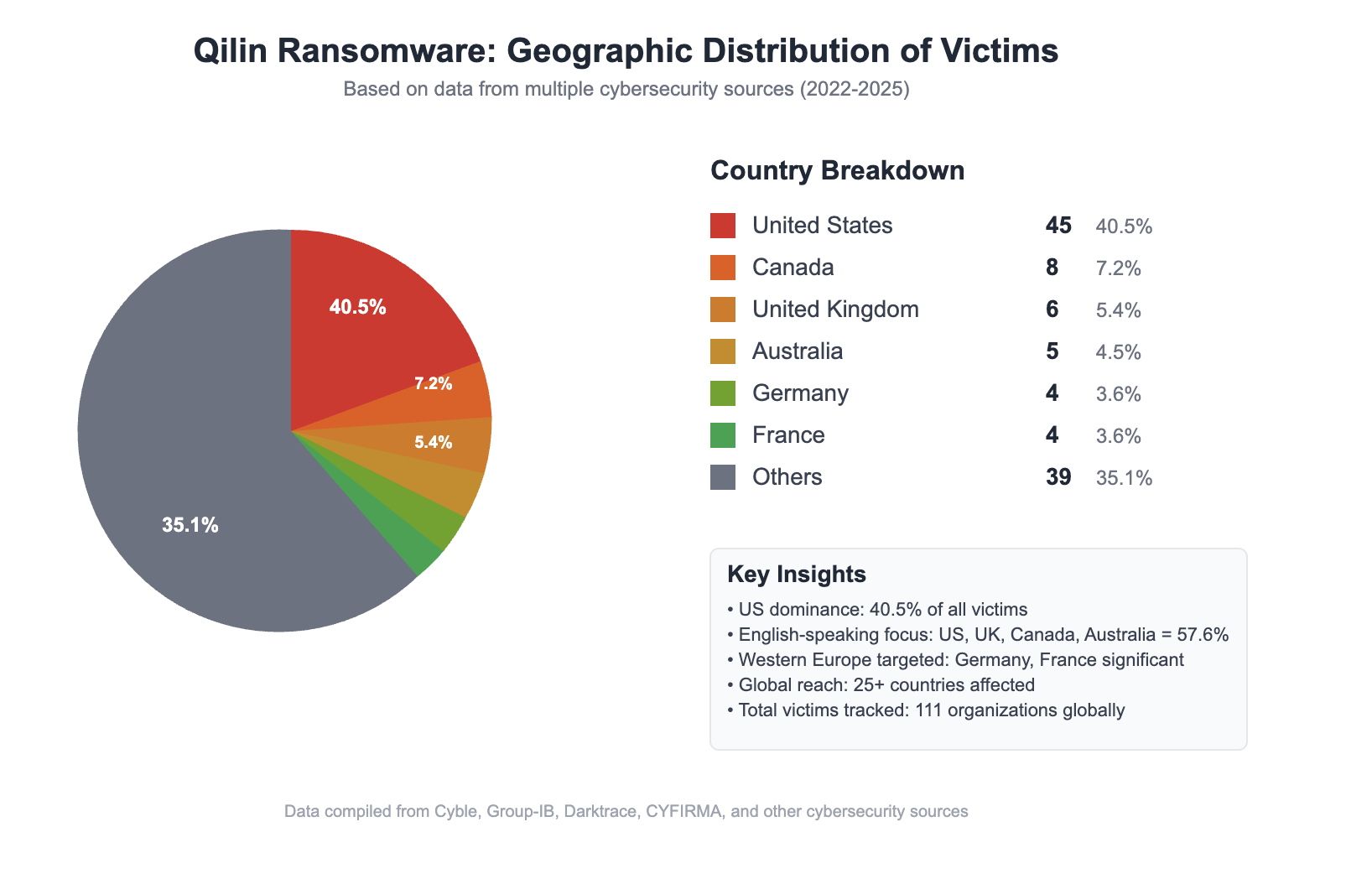
Targeting Strategy: Healthcare and Beyond
Qilin has demonstrated a particularly troubling focus on healthcare organisations, recognising that these entities face unique pressures that make them more likely to pay ransoms quickly. The group's targeting strategy reveals a calculated approach:
Healthcare Sector Emphasis: Hospitals, healthcare networks, and medical device manufacturers represent a significant portion of Qilin's victims. The group understands that disruptions to healthcare services can be life-threatening, creating enormous pressure to restore operations quickly.
Critical Infrastructure: Beyond healthcare, Qilin targets organizations in sectors deemed critical infrastructure, including energy, transportation, and manufacturing companies where operational disruption carries severe consequences.
Geographic Distribution: While initially focused on Western targets, Qilin has expanded globally, with victims spanning North America, Europe, Asia, and Australia, demonstrating the group's international reach and ambitions.
The Double Extortion Evolution
Qilin has refined the double extortion model to maximize pressure on victims:
Data Exfiltration First: Before deploying ransomware, operators spend considerable time identifying, copying, and exfiltrating sensitive data. This includes financial records, customer information, intellectual property, and any data that could prove embarrassing or damaging if released.
Leak Site Operations: The group maintains professional-looking leak sites where they publish stolen data from non-paying victims. These sites serve both as proof of their capabilities and as a deterrent to other potential victims considering non-payment.
Escalation Tactics: Qilin employs a tiered approach to pressure, beginning with private negotiations and escalating to public data releases, media outreach, and even direct contact with customers and partners of victim organisations.
The Legal Advisory Service: Criminalising Professional Services
Perhaps most disturbing is Qilin's provision of legal advisory services to their affiliates—a development that represents a new level of sophistication in ransomware operations. This service includes:
Data Valuation Expertise: Qilin provides affiliates with guidance on assessing the value of stolen data, helping them determine appropriate ransom demands based on the sensitivity and commercial value of compromised information.
Regulatory Knowledge: The group offers advice on which regulatory frameworks apply to different types of data breaches, helping affiliates understand the additional pressure points they can leverage during negotiations.
Negotiation Strategy: Legal advisors within the Qilin organisation provide guidance on negotiation tactics, helping affiliates maximise ransom payments while minimising the risk of law enforcement intervention.
Compliance Implications: The group educates affiliates on how various compliance requirements (GDPR, HIPAA, etc.) can be weaponised to increase pressure on victims, essentially turning regulatory frameworks into extortion tools.
This pseudo-legal infrastructure demonstrates how ransomware groups are evolving beyond simple criminal organisations into sophisticated business enterprises that mirror legitimate consulting operations.
The Human Cost
Behind the technical details and criminal innovation lies a stark human reality. Qilin's attacks have:
- Forced hospitals to divert ambulances and cancel surgeries
- Compromised the personal information of millions of individuals
- Caused billions of dollars in direct costs and economic disruption
- Threatened critical infrastructure that communities depend upon
The group's targeting of healthcare organisations is particularly egregious, as these attacks can directly impact patient care and potentially endanger lives.
Defense and Mitigation Strategies
Organisations must adopt a comprehensive approach to defend against sophisticated threat actors like Qilin:
Network Segmentation: Implementing robust network segmentation can limit an attacker's ability to move laterally and access critical systems.
Backup and Recovery: Maintaining secure, regularly tested backups stored offline or in immutable storage can reduce the impact of successful ransomware attacks.
Endpoint Detection and Response: Advanced EDR solutions that can detect behavioural anomalies and living-off-the-land techniques are essential for early detection.
User Education: Regular training on phishing recognition and safe computing practices remains a critical defensive measure.
Incident Response Planning: Organisations must have tested incident response plans that specifically address ransomware scenarios, including communication protocols and decision-making frameworks.
The Broader Implications
The evolution of groups like Qilin represents a troubling trend in cybercrime. The incorporation of legal advisory services, professional-grade infrastructure, and sophisticated business processes suggests that ransomware operations are becoming increasingly institutionalised.
This evolution poses significant challenges for law enforcement and cybersecurity professionals. As these groups become more sophisticated and business-like, they also become more resilient and harder to disrupt. The provision of legal advisory services, in particular, demonstrates how criminal organizations are adapting legitimate business practices for illicit purposes.
Looking Forward
The Qilin ransomware group represents the cutting edge of criminal innovation in cyberspace. Their combination of technical sophistication, business acumen, and ruthless targeting of vulnerable sectors makes them one of the most dangerous threat actors operating today.
Organisations must recognise that they face not just opportunistic criminals, but sophisticated adversaries operating with business-like efficiency and resources. The fight against ransomware requires not just technical defences, but a comprehensive approach that includes international cooperation, regulatory action, and industry-wide collaboration.
As Qilin and similar groups continue to evolve, the cybersecurity community must remain vigilant and adaptive. The stakes are too high—and the human cost too great—to do otherwise. The future of digital security depends on our ability to stay ahead of these evolving threats and protect the critical systems upon which modern society depends.
Understanding threats like Qilin is the first step in building effective defences. Organisations should work with cybersecurity professionals to assess their risk posture and implement appropriate protective measures against these sophisticated adversaries.
Related Posts
- All
- Cybersecurity
- How To Guides
- Ransomware Insights
- Security Insights



