Cyber Security
Offensive and Defensive AI: Let’s Chat(GPT) About It
ChatGPT: Productivity tool, great for writing poems, and… a security risk?! In this article, we show how threat actors can exploit ChatGPT, but also how defenders can use it for leveling up their game.
ChatGPT is the most swiftly growing consumer application to date. The extremely popular generative AI chatbot has the ability to generate human-like, coherent and contextually relevant responses.
Everything you need to know about IRAP
Introduction In this article I will take you through everything you need to know about an IRAP assessment and how to successfully achieve IRAP Accreditation; what it is, what’s involved, why it’s important and a checklist of things you will need to do to kick start your IRAP journey. What is the Information Security…
Read MoreGenerative AI – AI for the future
I recently attended a very informative and interesting talk on “Generative AI – AI for the Future” hosted by KWM and Professor Genevieve Bell from the Australian National University. A lot has been written about AI and many will be excused from thinking that AI is a modern innovation or simply ChatGPT but the history…
Read MoreDEF CON 31 – New Novel WFP filter attack for privilege escalation
I recently returned from the DEF CON 2023 conference in Las Vegas and amongst many of the briefings that I attended the talk by Ron Ben Yizhak was particularly interesting. His talk was called “#NoFilter – Abusing Windows Filtering Platform for Privilege Escalation”. Whilst privilege escalation attacks are fairly common against the Windows platform…
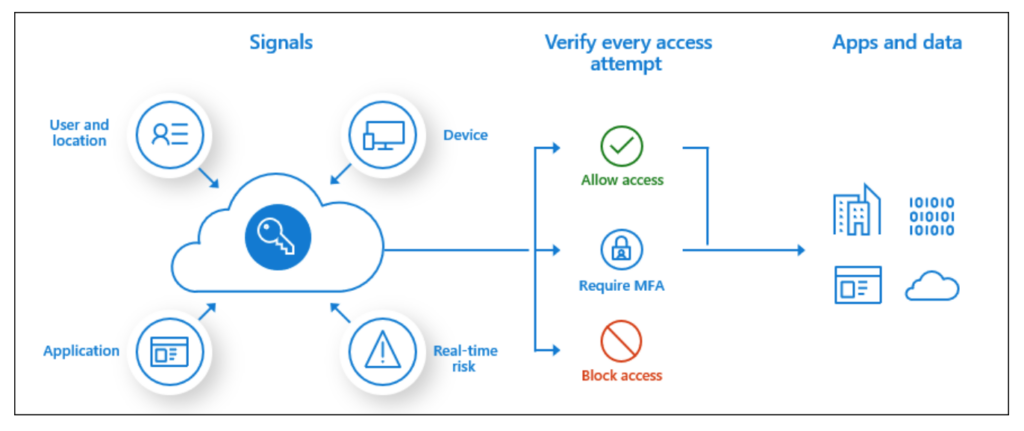
Read MoreWhy you need Azure Conditional Access Policies
Overview Having undertaken a number of Red Team assessments over the last 5 years, one of the common things that is uncovered during these assessments is the lack of robust Microsoft Azure AD conditional access policies. Microsoft Azure AD Conditional access is a premium feature and disabled by default. To enable it you need a…
Read MoreCyber insurance premiums soar
Cyber attacks are not going away anytime soon and in the wake of the Optus, Medibank and more recent Latitude Financial breach, the demand for cyber insurance has increased, despite premiums soaring as much as 300%. Many small to medium size businesses are feeling the affect and may now find it impossible to obtain cyber…
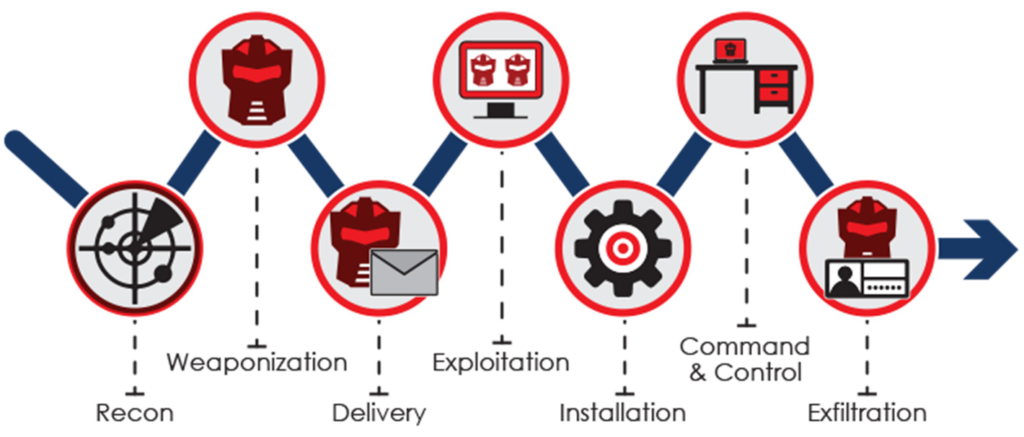
Read MoreDisrupting the Kill Chain
Over the last 10 years I’ve often heard the expression that… “Hackers only have to get it right once whilst defenders have to get it right all the time!” Well I don’t believe that’s entirely true and in fact I know it isn’t and in this article I’ll explain why! However good an attacker is…
Read MoreAs easy as 123456 !
Data security breaches have become common place over the last 10 years, so much so that as an industry we have almost become immune to them. However a recent study carried out by a Turkish Security researcher, Ata Hakcil, on password reuse found after analysing over a billion credentials that “123456” was the most…
Read More