Disrupting the Kill Chain
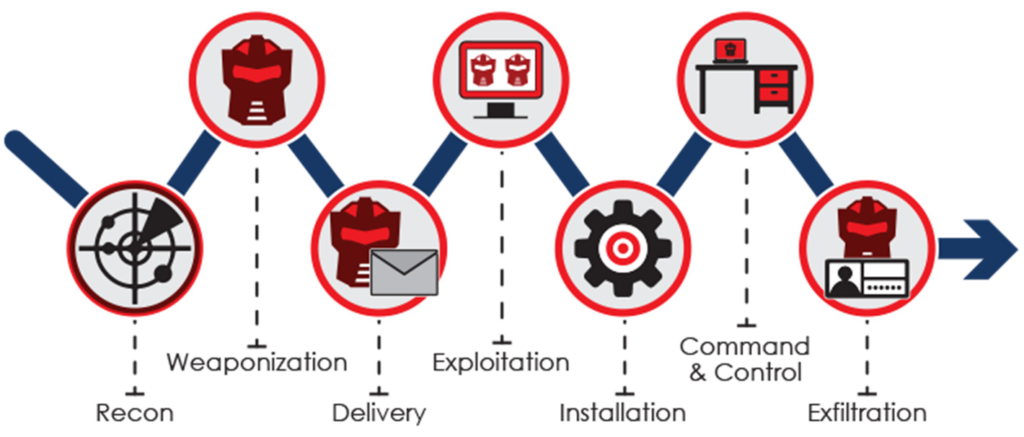
Over the last 10 years I've often heard the expression that...
"Hackers only have to get it right once whilst defenders have to get it right all the time!"
Well I don't believe that's entirely true and in fact I know it isn't and in this article I'll explain why!
However good an attacker is they will always leave digital breadcrumbs behind and if you know where to look you will find them. Using techniques from the world of DFIR is going to help you find these digital footprints and whilst the below list is by no means complete it will show you the Top 10 artefacts that you need to focus on.
Finding the needle in the haystack
Looking for attackers using everyday tools in your environment for the wrong reasons is a daunting task and something that would be impossible by manually looking through windows security logs. So having a SIEM and setting it up in the right way to detect and trigger on unusual events is essential.
What to monitor?
-
- Changes to high value admin groups in your domain. So Domain Admins, Exchange Admins, Schema Admins and others.
-
- Credential Dumping
-
- Unusual PowerShell Usage
-
- Unusual Command Line Usage
-
- DNS Tunneling
-
- Fast Flux DNS
-
- Process Injection
-
- DLL Search order Hi-jacking
-
- Registry run keys
-
- Suspicious network activity (look for use of rundll32.exe)
Once you have your rules configured to search for the above criteria, adding context by enriching events with further information will really help you to hone in on the target.
Contextual Information
As an example you could add Active Directory user meta data to an event to identify the user or you could add network information to identify the network location, floor, office location and add this to event.
Fine Tuning
Further fine tuning may be required to get the outcome you were expecting and to avoid alert fatigue!