Cyber Security
CrowdStrike Tries to Patch Things Up With Cybersecurity Industry
Both CrowdStrike president and CEO were at Black Hat and DEF CON to face direct questions from customers and cybersecurity professionals.
Read MoreUN Approves Cybercrime Treaty Despite Major Tech, Privacy Concerns
The treaty would allow any country to request technology firms to aid in cybercrime investigations and preserve data about their users — potentially imperiling penetration testers and security researchers, among others.
Read MoreAustralian gold producer Evolution Mining hit by ransomware
Evolution Mining has informed that it has been targeted by a ransomware attack on August 8, 2024, which impacted its IT systems. […]
Read MoreCriminal IP and Maltego Join Forces for Enhanced Cyber Threat Search
AI SPERA announced today that its IP address intelligence engine, Criminal IP, can now be integrated with Maltego’s unified user interface and is available on the Maltego’s marketplace, […]
Read MoreNew Malware Hits 300,000 Users with Rogue Chrome and Edge Extensions
An ongoing, widespread malware campaign has been observed installing rogue Google Chrome and Microsoft Edge extensions via a trojan distributed via fake websites masquerading as popular software.
“The trojan malware contains different deliverables ranging from simple adware extensions that hijack searches to more sophisticated malicious scripts that deliver local extensions to steal private data
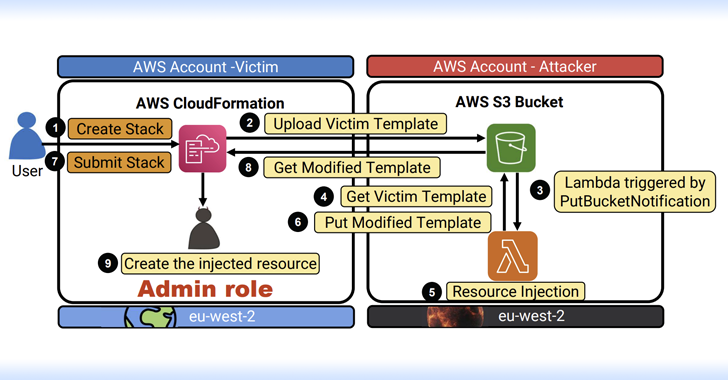
Experts Uncover Severe AWS Flaws Leading to RCE, Data Theft, and Full-Service Takeovers
Cybersecurity researchers have discovered multiple critical flaws in Amazon Web Services (AWS) offerings that, if successfully exploited, could result in serious consequences.
“The impact of these vulnerabilities range between remote code execution (RCE), full-service user takeover (which might provide powerful administrative access), manipulation of AI modules, exposing sensitive data, data
Microsoft discloses Office zero-day, still working on a patch
Microsoft has disclosed a high-severity zero-day vulnerability affecting Office 2016 and later, which is still waiting for a patch. […]
Read MorePrudential Financial now says 2.5 million impacted by data breach
Prudential Financial, a global financial services company, has revealed that over 2.5 million people had their personal information compromised in a February data breach. […]
Read MoreCDK Global says all dealers will be back online by Thursday
CDK Global says that its dealer management system (DMS), impacted by a massive IT outage following a June 18th ransomware attack, will be back online by Thursday for all car dealerships. […]
Read MoreAustralian charged for ‘Evil Twin’ WiFi attack on plane
An Australian man was charged by Australia’s Federal Police (AFP) for allegedly conducting an ‘evil twin’ WiFi attack on various domestic flights and airports in Perth, Melbourne, and Adelaide to steal other people’s email or social media credentials. […]
Read More