Security News
Getting gooey with GULOADER: deobfuscating the downloader
Elastic Security Labs walks through the updated GULOADER analysis countermeasures.
Read MoreGenerative AI Security: Preventing Microsoft Copilot Data Exposure
Microsoft Copilot has been called one of the most powerful productivity tools on the planet.
Copilot is an AI assistant that lives inside each of your Microsoft 365 apps — Word, Excel, PowerPoint, Teams, Outlook, and so on. Microsoft’s dream is to take the drudgery out of daily work and let humans focus on being creative problem-solvers.
What makes Copilot a different beast than ChatGPT and
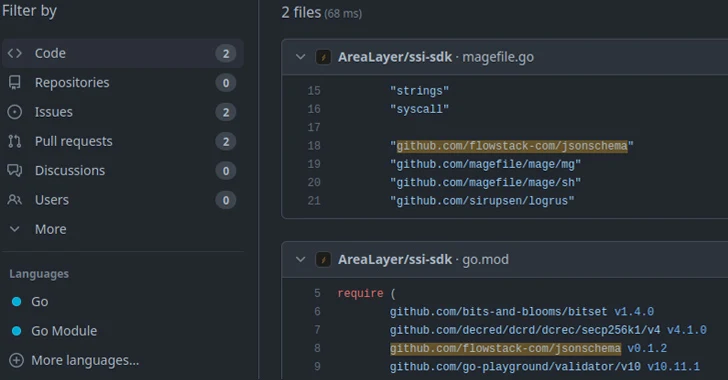
15,000 Go Module Repositories on GitHub Vulnerable to Repojacking Attack
New research has found that over 15,000 Go module repositories on GitHub are vulnerable to an attack called repojacking.
“More than 9,000 repositories are vulnerable to repojacking due to GitHub username changes,” Jacob Baines, chief technology officer at VulnCheck, said in a report shared with The Hacker News. “More than 6,000 repositories were vulnerable to repojacking due to account
‘AeroBlade’ Group Hacks US Aerospace Company
Aeroblade flew under the radar, slicing through detection checks on a quest to steal sensitive commercial data.
Read MoreRussian hackers exploiting Outlook bug to hijack Exchange accounts
Microsoft’s Threat Intelligence team issued a warning earlier today about the Russian state-sponsored actor APT28 (aka “Fancybear” or “Strontium”) actively exploiting the CVE-2023-23397 Outlook flaw to hijack Microsoft Exchange accounts and steal sensitive information. […]
Read MoreDecember Android updates fix critical zero-click RCE flaw
Google announced today that the December 2023 Android security updates tackle 85 vulnerabilities, including a critical severity zero-click remote code execution (RCE) bug. […]
Read MoreOver 20,000 vulnerable Microsoft Exchange servers exposed to attacks
Tens of thousands of Microsoft Exchange email servers in Europe, the U.S., and Asia exposed on the public internet are vulnerable to remote code execution flaws. […]
Read MoreJapan’s Space Program at Risk After Microsoft Active Directory Breach
The agency, known as JAXA, has shut down parts of its network as it conducts an investigation to discover the scope and impact of the breach.
Read MoreNorth Korea’s Lazarus Group Rakes in $3 Billion from Cryptocurrency Hacks
Threat actors from the Democratic People’s Republic of Korea (DPRK) are increasingly targeting the cryptocurrency sector as a major revenue generation mechanism since at least 2017 to get around sanctions imposed against the country.
“Even though movement in and out of and within the country is heavily restricted, and its general population is isolated from the rest of the world, the regime’s
Iranian Hackers Exploit PLCs in Attack on Water Authority in U.S.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) revealed that it’s responding to a cyber attack that involved the active exploitation of Unitronics programmable logic controllers (PLCs) to target the Municipal Water Authority of Aliquippa in western Pennsylvania.
The attack has been attributed to an Iranian-backed hacktivist collective known as Cyber Av3ngers.
“Cyber threat