Data Security and Privacy: Time to act is now!

With the latest Data Privacy law reforms on the horizon and having just finished off Privacy Awareness Week, #PAW2024, in Australia this article is aimed at all organisations that hold sensitive data.
Data breaches are nasty, and they impact everyone involved. Australia has seen some of the largest data breaches over the last 18 months. Only last week, FirstMac / Loans.com.au issued a statement to say they had been the victim of the Embargo Ransomware group at the end of April. Unfortunately, my details were caught up in that breach, having been a previous customer of theirs some 5 years ago.
Like me, you may have been caught up in a similar data breach yourself, and understandably, you may have been angry, confused, upset, and not knowing initially at least what to do. The main thing is not to panic until you get confirmation of what details may have been stolen. I'm not going to provide advice in this article about what to do, as plenty of information is already out there about practical steps you can undertake to safeguard your identity going forward.
While you may have a reasonable grasp of the type of data you hold, knowing where it is and who has access to it across your entire organisation is very challenging. Particularly if you have been holding data for decades and storing it in offsite archives, cloud storage, with 3rd party suppliers and others the story becomes even more complex.
So where should you start?
Here is a six step process that you can follow to get you get started.
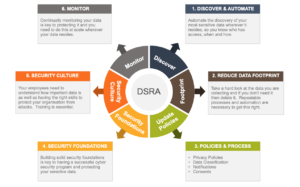
Cyooda Security - Data Security Risk Assessment
- Discover and Automate where your data resides.
- Reduce your data footprint - data breaches have highlighted that all too often organisations keep sensitive data beyond its sell by date.
- Get your policies, procedures and processes in order
- Security foundations - get the right mix of people, process and technology working together to create a robust and effective security regime for your business.
- Security Culture - Train your people on all matters of data privacy, sensitive document handling, appropriate use of classification labels and how to spot malicious phishing emails.
- Monitor - Continuous monitoring is essential to protecting your sensitive data, especially at scale and across cloud environments.
If you would like to find out more you can download this free resource below that we have put together that explains the latest Privacy Reforms, What you need to do and how to get started to protect your data.
Data Security and Privacy Solutions Guide