Endpoint Security Part 4: How to create a playbook to isolate a machine and alert your SOC team

Overview
In this fourth article of a 5 part series on 'Endpoint Security' I'm going to be showing you how to create a rule in your Elastic SIEM to generate an alert and isolate a host if the presence of malware is detected.
Step One - Create the detection rule
In your Kibana console select: Security | Rules | Detection Rules (SIEM)
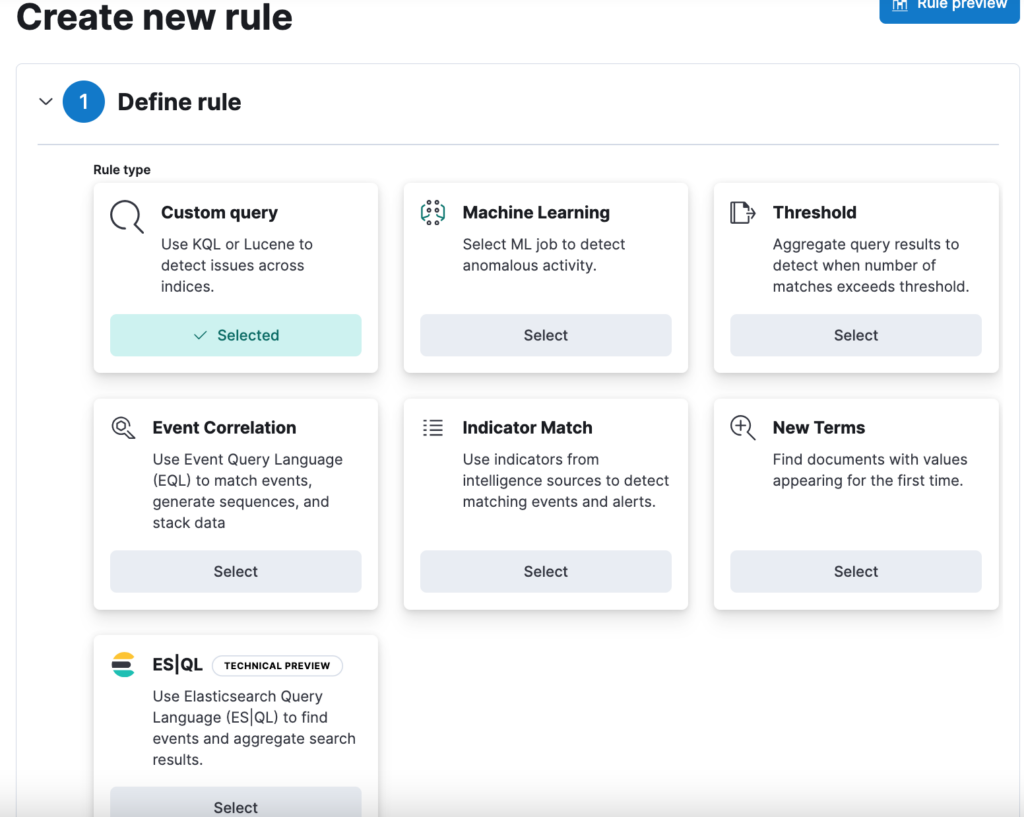
Then in the Define Rule section select: Custom query.
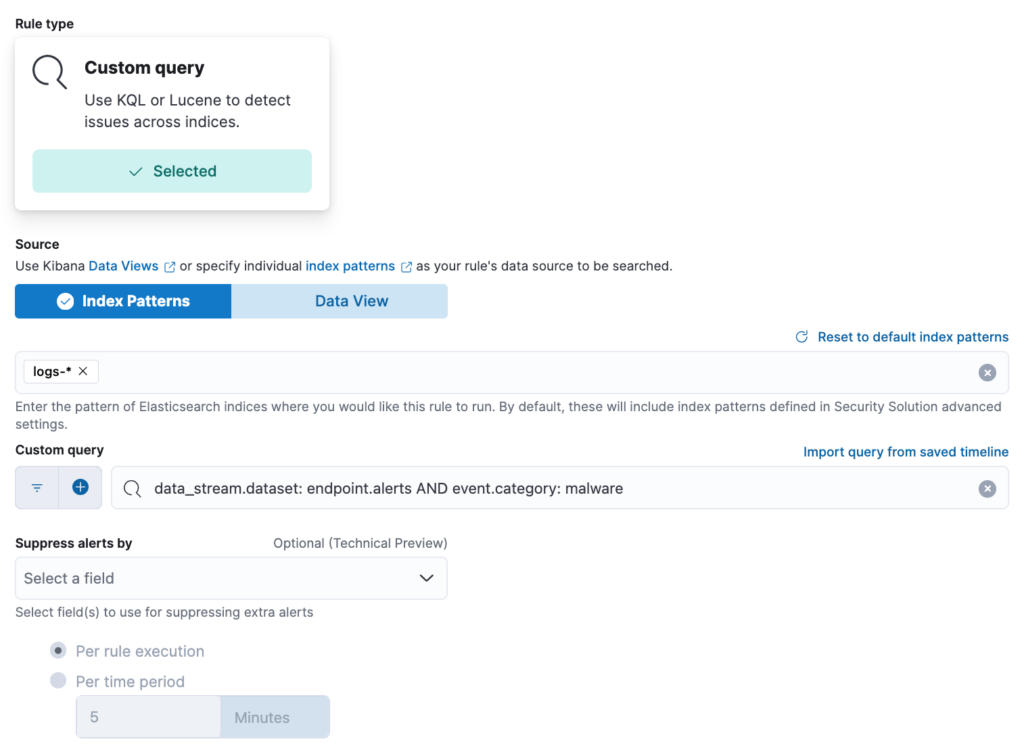
In the custom query section provide an index patern, custom query to detect the event. In our case this is all endpoint alerts with the category malware.
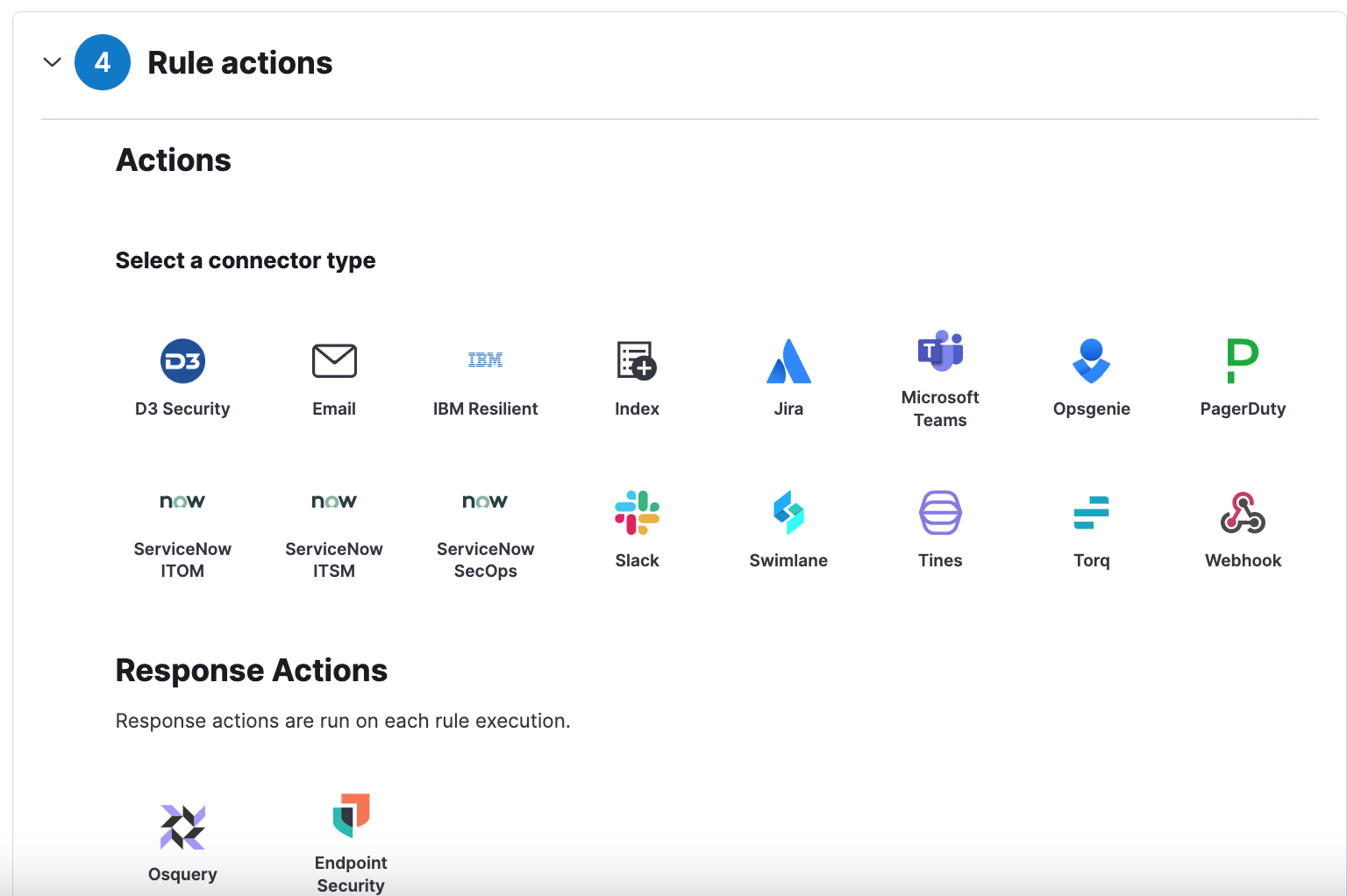
Step Two - Configure the Alert
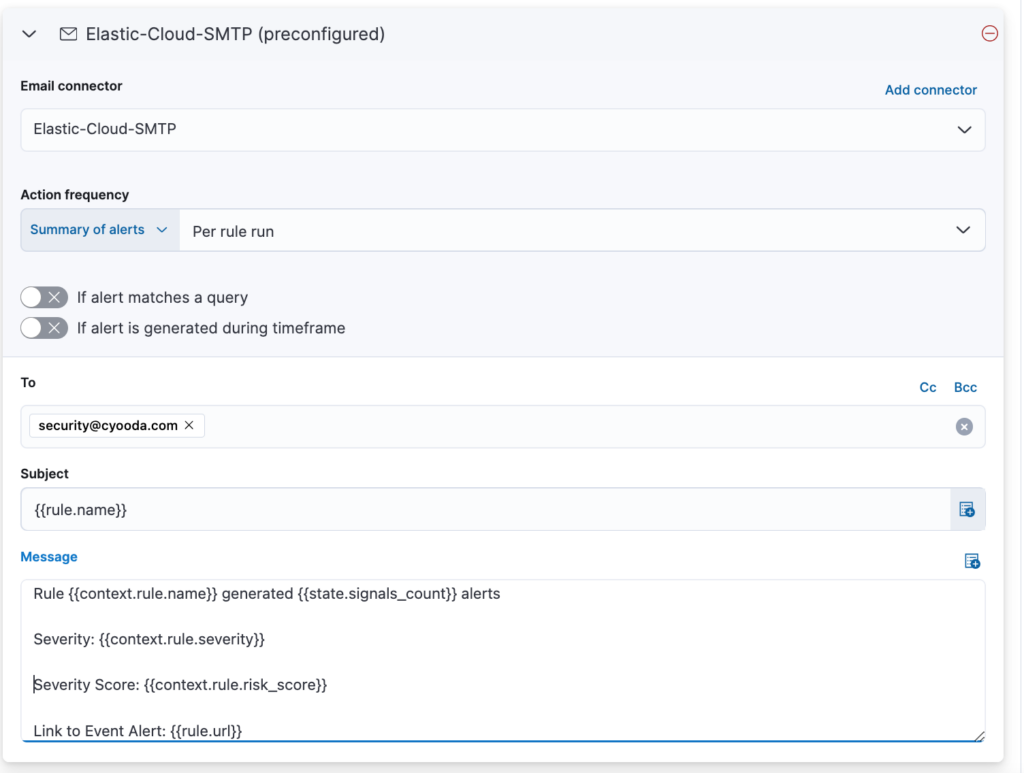
Next configure the Rule actions to Alert. In this example we will select the Email connector type ad complete the required fields. If you click on the + symbol next to the Subject and Message you can select labels that will pre-populate data from the actual event.
Step Three - Configure the Action to Isolate the host
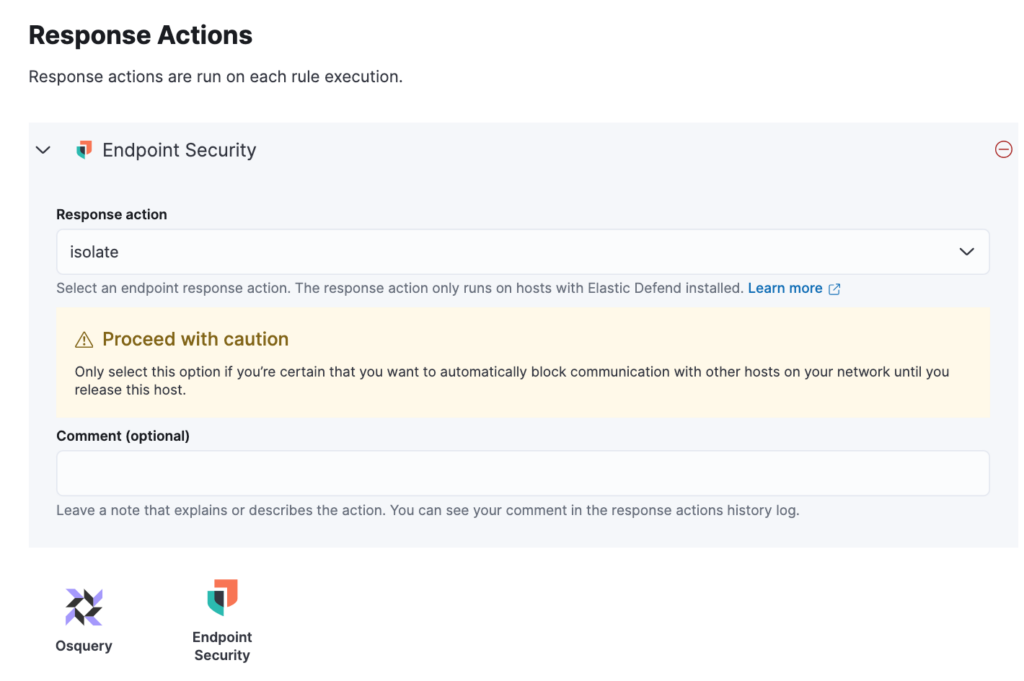
Next select the Response Actions and from the 'Endpoint Security Response Action' drop down select 'Isolate' which will Isolate the host when the rule is triggered.
Step Four - Trigger the Alert
To trigger alert I am going to use a 'Test' Malware file from Palo Alto Networks. I have configured my Elastic Endpoint Security agent to display a visual pop-up message if malware is detected. When the test file is executed we will see the following pop-up:
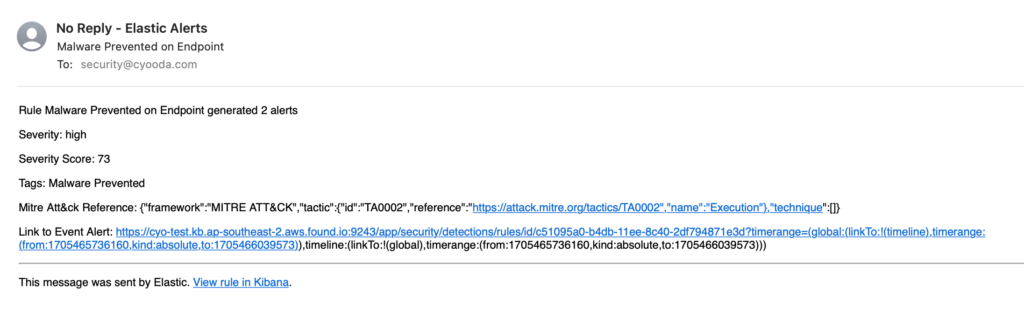
After a couple of minutes the rule will trigger on the SIEM and we should then receive an email alert as well as the host being isolated.
Once the host is isolated, if this was a real security event you would need to call the user to find out what they were doing and gather further information to determine the next course of action.
That's it for now!
You now have a detection rule in place that will trigger an email alert and also isolate the host for further investigation. This is a fairly simple use case and next time I will be showing you how you can use automation workflows in the form of 'Tines' to create additional workflow actions.