How To: Email Phishing, malicious payload analysis walkthrough
The other day I received a malicious phishing email with what appeared to be an invoice but in fact was a javascript embedded in an HTML document.
So let's get into it.
Initial Inspection
When I initially opened the document in my visual code editor it appeared as follows:
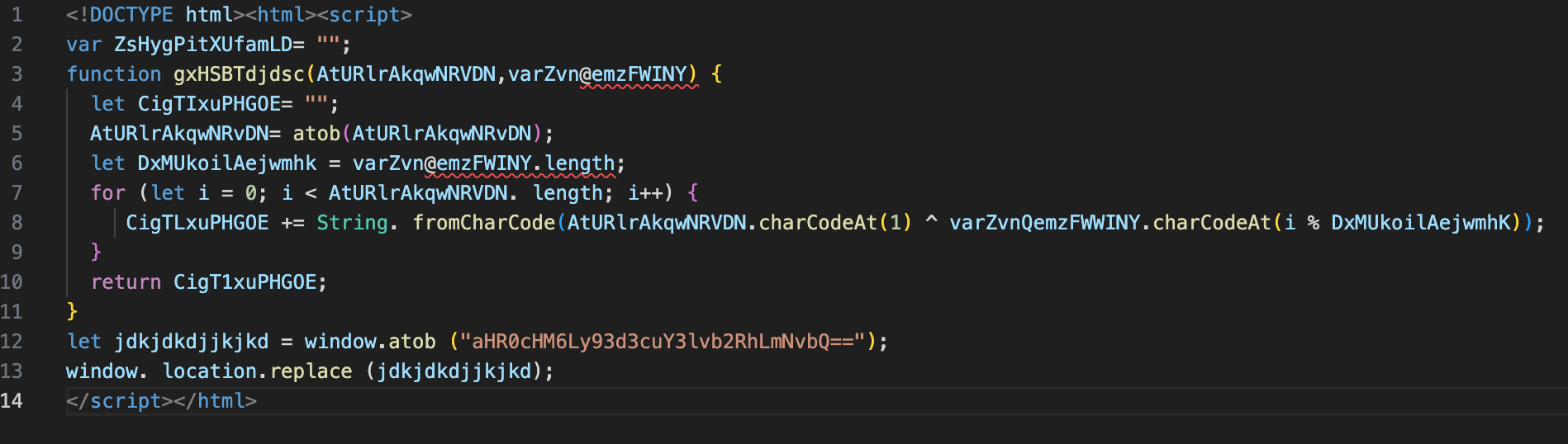
The second line declares a variable but doesn't appear to do anything and is not used in the script.
The function takes 2 parameters and it is unclear at first glance from the naming convention of all variable in the script the true intent of the code. But clearly it is using characteristics associated with malicious intent:
- Obfuscation
- Decoding - shown in lines 5 and 12 with the 'atob' function used to decode a base64 encoded string.
The decoded string in line 12 is a URL, which the user is then redirected to.
If you place the string in line 12 into CyberChef which is a great tool to assist with tasks such as this you can decode the string from base64 to plain text which confirms the function is being used for that purpose.
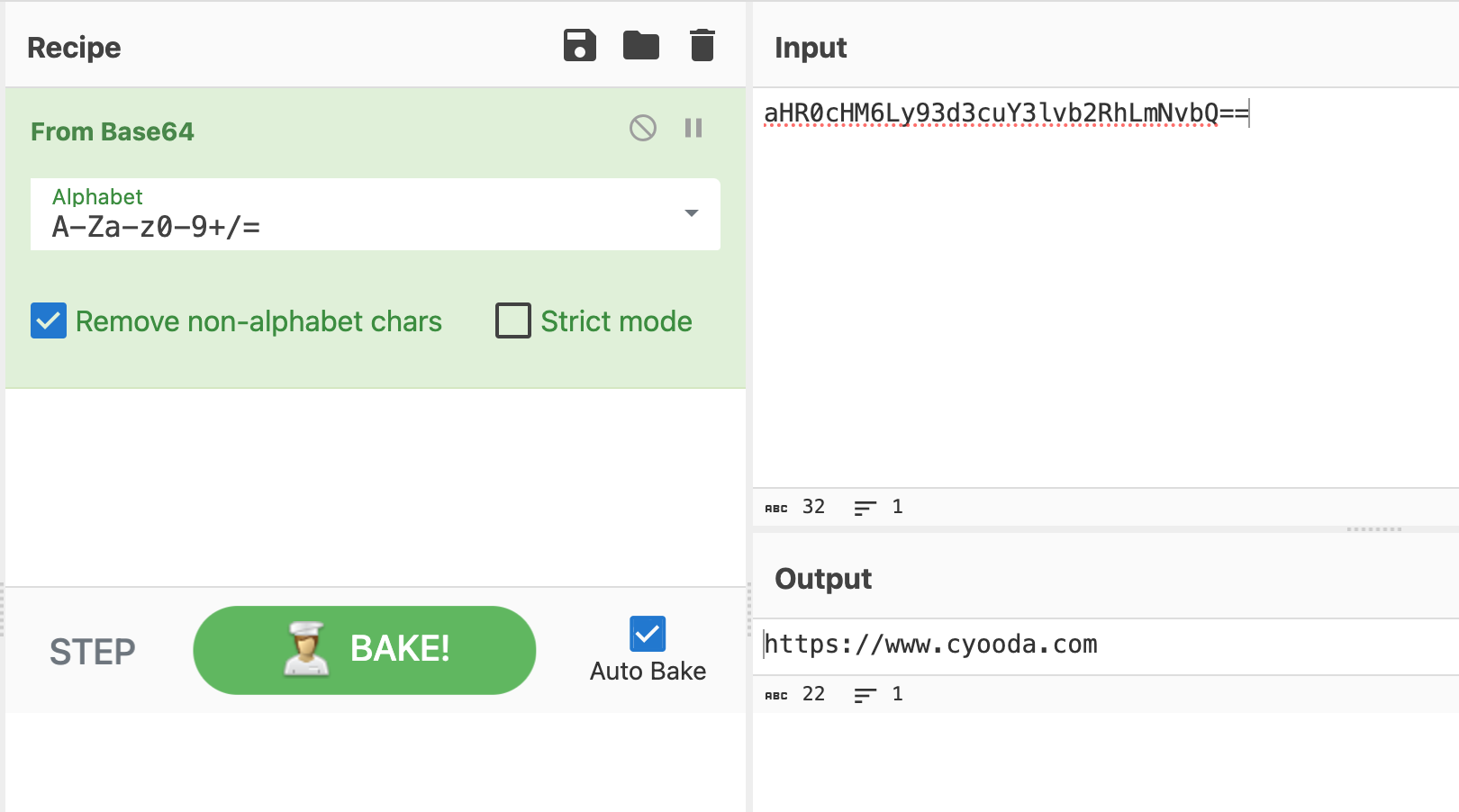
In summary, the code tries to hide its true intent by defining a function that XORs characters from two strings and returns the result. Then, it decodes a Base64-encoded URL and redirects the browser to that URL. In this case, the URL is malicious.
NOTE: I removed the original base64 encoded string from the code to remove any risk and replaced with my own URL.