NSA shares zero-trust guidance to limit adversaries on the network

Original Source: Bleeping Computer
The National Security Agency is sharing new guidance to help organizations limit an adversary's movement on the internal network by adopting zero-trust framework principles.
A zero-trust security architecture requires strict controls for accessing resources on the network, be they inside or outside the physical perimeter, to minimize the impact of a breach.
Compared to the traditional IT security model, which presumes that everything and everyone on the network is trusted, the zero-trust design assumes that a threat already exists and does not allow free rein inside the network.
Advancing the zero-trust maturity is done gradually by addressing various components, or pillars, that threat actors can leverage in an attack.
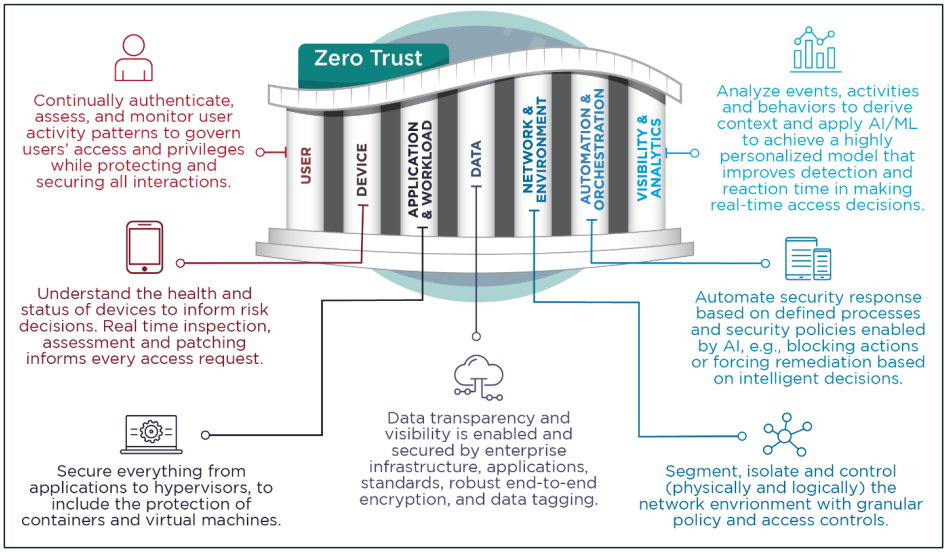
source: National Security Agency
The NSA released today zero-trust guidance for the network and environment component, which comprises all hardware and software assets, non-person entities, and inter-communication protocols.
The zero-trust model delivers in-depth network security through data flow mapping, macro and micro segmentation, and software-defined networking.
For each of them, an organization must reach a specific maturity level that allows them to continue building according to the zero-trust principles.
"The network and environment pillar isolates critical resources from unauthorized access by defining network access, controlling network and data flows, segmenting applications and workloads, and using end-to-end encryption" - National Security Agency (PDF)
Data flow mapping starts with identifying where and how the data is stored and processed. Advanced maturity in this case is achieved when the organization has a full inventory and visibility of the flow and can mitigate all current, new, or anomalous routes.
Through macro segmentation, organizations can limit lateral movement on the network by creating network areas for users in each department.
As an example, someone in accounting does not need access to the network segment dedicated to human resources unless explicitly required, so a threat actor would have a limited attack surface to pivot to.
With micro segmentation, the management of the network is broken down into smaller components, and strict access policies are implemented to limit lateral data flows.
The NSA explains that "micro segmentation involves isolating users, applications, or workflows into individual network segments to further reduce the attack surface and limit the impact should a breach occur."
More granular control over micro segmentation is achieved through software-defined networking (SDN) components, which can provide customizable security monitoring and alerting.
SDN allows controlling packet routing from a centralized control center, provides better visibility into the network, and permits enforcing policies for all network segments.
For each of the four components in the network and environment pillar of the zero-trust architecture, the NSA describes four levels of maturity, from the preparation step to the advanced phase where extensive controls and management systems are implemented to allow optimal visibility, monitoring, and to ensure the growth of the network.
Designing and building a zero-trust environment is a complex task that requires going through maturity stages systematically.
Done properly, the result is an enterprise architecture that can resist, identify, and respond to threats attempting to exploit weaknesses.
The NSA released the first guide for the zero-trust framework in February 2021 (Embracing a Zero Trust Security Model), which describes the model and the advantages of the principles behind it.
In April 2023, the agency released guidance for reaching the maturity of the user component in the zero-trust framework - Advancing Zero Trust Maturity Throughout the User Pillar.
Source URL: https://www.bleepingcomputer.com/news/security/nsa-shares-zero-trust-guidance-to-limit-adversaries-on-the-network/
Author: