Posts by John Reeman
Vulnerability Management Metrics: How to be effective
🔒Implementing a robust Vulnerability Management Program is a critical step in strengthening your organisation’s cyber defences. But how do you determine its effectiveness? Success cannot be measured merely by the number of vulnerabilities identified or patches applied.🔒 Key metrics can provide a clear picture of your program’s performance and effectiveness. Here are a few critical…
Read MoreData Privacy: What is Personally Identifiable Information (PII)?
What is Personally Identifiable Information (PII) In a world where personal information is constantly being shared and disseminated online, protecting your privacy has become more important than ever. Understanding what constitutes Personally Identifiable Information (PII) is crucial in safeguarding your sensitive data. From your name and address to your superannuation number and banking details, PII…
Read MoreVirtual CISO for hire: Build cyber security resilience
As cybersecurity threats continue to evolve and become more sophisticated, organizations must stay one step ahead to protect their valuable data and assets. In today’s digital landscape, the role of a Chief Information Security Officer (CISO) is vital in ensuring the security of an organisation’s systems and information. However, not every organisation has the resources…
Read MoreDemystifying an IRAP Assessment: Everything You Need to Know
Are you a business owner looking to understand the ins and outs of the IRAP assessment? Look no further! In this comprehensive guide, we will demystify the IRAP assessment and provide you with everything you need to know. The IRAP assessment, or Information Security Registered Assessors Program, is a crucial step in ensuring the security…
Read MoreData Privacy in Australia: Safeguard Your Personal Data
Data privacy has become a critical concern for individuals and businesses in an increasingly interconnected digital world. Nowhere is this more evident than in Australia, where safeguarding online information is paramount. With cyber threats increasing and data breaches becoming more frequent, protecting sensitive data has become imperative for Australians. In this article, we delve into…
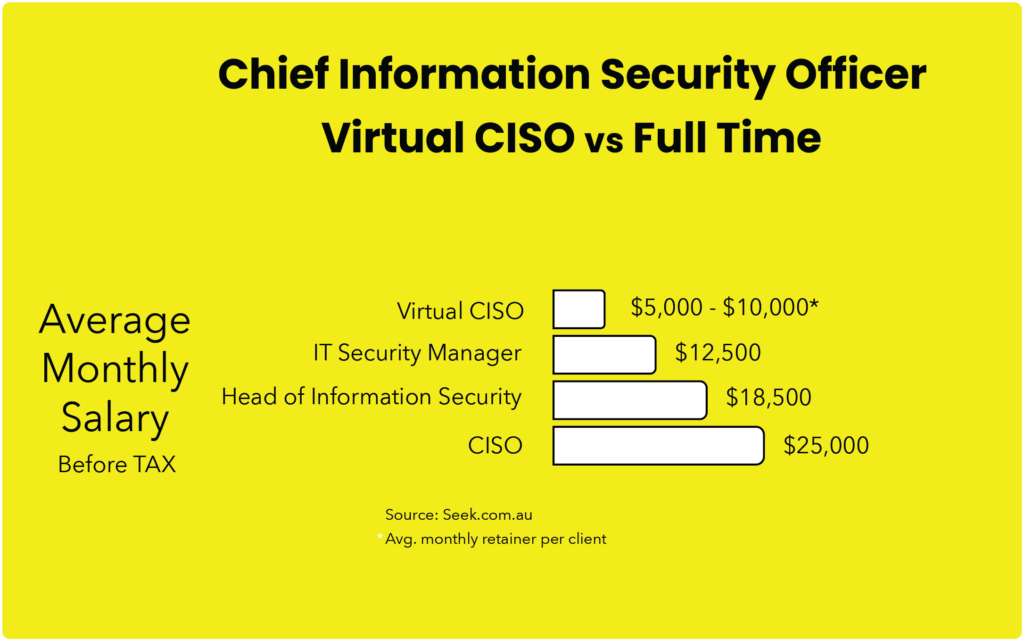
Read MoreWhy having a Virtual CISO is important for your business?
Virtual CISO Services Australia 💼 Small to medium-sized businesses (SMBs) often underestimate their vulnerability to cyber threats, primarily because they lack the necessary tools and expertise to protect against these risks. That’s where a 𝐕𝐢𝐫𝐭𝐮𝐚𝐥 𝐂𝐈𝐒𝐎 (Chief Information Security Officer) comes into play! 💼 A Virtual CISO is not only a cost-effective solution, but they…
Read MoreHow to build a successful cybersecurity program
In this video I will be taking you through a cybersecurity framework that I have developed and perfected over the last 25 years to help organisations build strong cybersecurity programs, reduce risk and remain safe. Ready to find out more? Book in a Call
Read MoreData Security and Privacy: Time to act is now!
With the latest Data Privacy law reforms on the horizon and having just finished off Privacy Awareness Week, #PAW2024, in Australia this article is aimed at all organisations that hold sensitive data. Data breaches are nasty, and they impact everyone involved. Australia has seen some of the largest data breaches over the last 18 months.…
Read MoreTo be or not to be a CISO
Do you aspire to be a CISO? As a former CISO, I felt compelled to write this article after seeing many articles about the role of a CISO and opinions on how hard it is becoming. I’m uncertain whether many people today would actually aspire to be a CISO given the pressures, the demands of…
Read MoreHow To: Email Phishing, malicious payload analysis walkthrough
The other day I received a malicious phishing email with what appeared to be an invoice but in fact was a javascript embedded in an HTML document. So let’s get into it. Initial Inspection When I initially opened the document in my visual code editor it appeared as follows: The second line declares a variable…
Read More