Data Privacy: What is Personally Identifiable Information (PII)?

What is Personally Identifiable Information (PII)
In a world where personal information is constantly being shared and disseminated online, protecting your privacy has become more important than ever. Understanding what constitutes Personally Identifiable Information (PII) is crucial in safeguarding your sensitive data.
From your name and address to your superannuation number and banking details, PII encompasses any information that can be used to identify an individual. This includes email addresses, phone numbers, birthdates, and even biometric data.
With cyber threats on the rise, hackers and data breaches can pose a significant risk to your personal information. Repercussions of a PII breach can range from identity theft and financial loss to reputation damage and even legal consequences.
In this article, we will delve into the world of PII, discussing its definition, why it matters, and the steps you can take to protect your privacy. By gaining a deeper understanding of PII and its implications, organisation's can make informed decisions about the personal information they collect and use and take the necessary precautions to ensure it remains safe.
What qualifies as PII Data
The scope of Personally Identifiable Information (PII) extends far beyond just the traditional identifiers like names and addresses. In today's interconnected world, PII encompasses a wide range of data points that can be used to uniquely identify an individual. This includes but is not limited to email addresses, social media usernames, IP addresses, biometric information, and even geolocation data. The more pieces of PII that are gathered, the easier it becomes to build a comprehensive profile of an individual.
Moreover, seemingly innocuous details like a person's browsing history or purchase preferences can also be considered PII when combined with other data points. This interconnected nature of information poses a significant challenge when it comes to protecting one's privacy. Individuals must be vigilant not only about the data they willingly provide but also about the passive data collection that occurs as they navigate through the digital landscape.
From a business perspective, understanding what qualifies as PII is crucial for compliance with data protection regulations and maintaining the trust of customers. By adopting a broad view of PII data and implementing robust security measures, organisations can demonstrate their commitment to safeguarding sensitive information and upholding privacy standards.
Personally Identifiable Information (PII) and the Australian Data Privacy Law
In Australia, the protection of Personally Identifiable Information (PII) is governed by the Privacy Act of 1988, which outlines the obligations of organisations in relation to the collection, use, and disclosure of personal information. Under the Act, entities are required to handle PII in accordance with the Australian Privacy Principles (APPs), which set out specific standards for the management of personal data.
APP 11, in particular, pertains to security of personal information, mandating that organisations take reasonable steps to protect PII from misuse, interference, loss, unauthorised access, modification, or disclosure. Failure to comply with the APPs can result in penalties and reputational damage for businesses, highlighting the importance of prioritising data privacy and security.
By aligning their practices with the Australian Data Privacy Law, organisations can not only avoid legal repercussions but also build trust with their customers. Upholding the principles of transparency, accountability, and data minimisation can go a long way in fostering a culture of respect for privacy rights and promoting responsible data handling practices in the digital landscape.
Creating a Data Privacy Policy and Framework
Developing a comprehensive data privacy policy and framework is essential for organisations looking to safeguard Personally Identifiable Information (PII) and comply with data protection regulations. A data privacy policy serves as a roadmap for how an organisation collects, stores, processes, and shares personal information, outlining the procedures and protocols in place to protect PII from unauthorised access or disclosure.
When creating a data privacy policy, organisations should consider factors such as the types of PII collected, the purposes for which it is used, the security measures in place to protect it, and the procedures for responding to data breaches. By clearly articulating these aspects, organisations can establish a foundation for responsible data governance and demonstrate their commitment to protecting individual privacy rights.
In addition to a data privacy policy, implementing a robust data privacy framework involves establishing internal controls, conducting regular risk assessments, providing employee training on data security best practices, and engaging with third-party vendors who handle PII. By integrating data privacy into the core operations of the organisation, businesses can proactively address privacy risks and enhance trust with their stakeholders.
PII protection best practices
Safeguarding Personally Identifiable Information (PII) requires a multi-faceted approach that combines technical controls, organisational policies, and user awareness.
Data Security Risk Assessment
Conduct a Privacy Impact Assessment (PIA) or Data Security Risk Assessment (DSRA) to determine, for each type or classification of PII. Understand how it is collected, where it is stored, retention periods, and how it is disposed of.
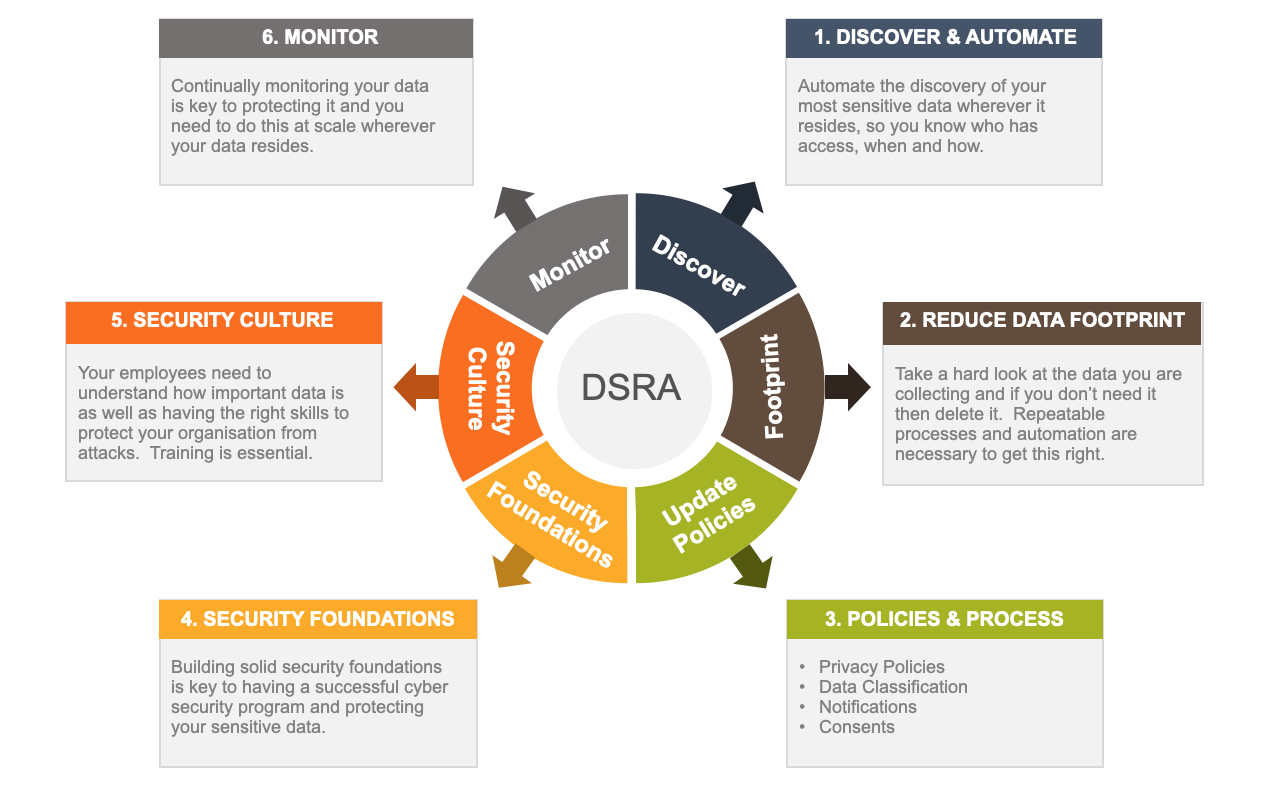
Governance
- Understand your organisations legal obligations for the countries it operates in.
- Assign roles and responsibilities in your organisation for privacy oversight
- Identify any voluntary standards you need to comply with
- Ascertain your organisation’s security and liability policy with regard to third party products and services e.g. cloud services (storage, compute etc)
Controls
Implementing encryption protocols to secure data both at rest and in transit is a fundamental best practice for protecting PII from unauthorised access. Encryption helps to render sensitive information unreadable to anyone without the proper decryption key, thereby reducing the risk of data breaches.
Furthermore, adopting strong authentication mechanisms such as multi-factor authentication (MFA) adds an extra layer of security to systems that store or process PII. By requiring users to provide multiple forms of verification before accessing sensitive data, organisations can significantly reduce the likelihood of unauthorised access or identity theft.
Regularly updating software and systems to patch known vulnerabilities, conducting penetration testing to identify weaknesses, and monitoring network traffic for suspicious activities are additional best practices for maintaining the security and integrity of PII. By staying informed about emerging threats and evolving security practices, organisations can stay one step ahead of cybercriminals and protect the confidentiality of personal information.
Risk Correlation
Think about how you correlate your risks.

Regulations and laws related to PII
In addition to the Australian Privacy Act, there are several other regulations and laws around the world that govern the protection of Personally Identifiable Information (PII). The European Union's General Data Protection Regulation (GDPR), for example, establishes stringent requirements for the handling of personal data and imposes heavy fines on organisations that fail to comply with its provisions. Under the GDPR, individuals have the right to access, correct, and delete their PII, as well as the right to be informed about how their data is being processed.
Similarly, the California Consumer Privacy Act (CCPA) grants California residents certain rights regarding their personal information and requires businesses to disclose their data collection practices. By understanding the various regulations that apply to PII, organisations can ensure they are meeting the necessary legal requirements and protecting the privacy rights of individuals.
Moreover, international frameworks such as the Asia-Pacific Economic Cooperation (APEC) Privacy Framework and the Organisation for Economic Co-operation and Development (OECD) Guidelines on the Protection of Privacy and Transborder Flows of Personal Data provide additional guidance on best practices for data protection and cross-border data transfers. By adhering to these frameworks, organisations can demonstrate their commitment to global privacy standards and promote trust in the digital economy.
Data Privacy Security Controls (APP 11)
Under the Australian Privacy Principles (APPs), specifically APP 11, entities are required to take reasonable steps to protect Personally Identifiable Information (PII) from misuse, interference, loss, unauthorised access, modification, or disclosure. This includes implementing appropriate security controls and safeguards to ensure the confidentiality and integrity of personal information. Organisations must assess the risks associated with the handling of PII and tailor their security measures accordingly.
Data privacy security controls encompass a variety of measures, including access controls, encryption, data minimisation, secure disposal practices, and incident response procedures.
Other areas to consider are:
- Data Loss Prevention
- Data Security Posture Management
- Data Masking
- Change Management
- Ethical Walls
- Privileged user access and monitoring
- Sensitive data access auditing
- Secure audit trail archiving
- User rights management
- User tracking
By restricting access to PII based on the principle of least privilege, organisations can reduce the likelihood of unauthorised disclosure or misuse of sensitive data. Encryption technologies, such as secure sockets layer (SSL) and transport layer security (TLS), help protect data in transit over networks and at rest in storage.
In the event of a data breach or security incident, having a robust incident response plan in place is crucial for containing the breach, mitigating the impact, and notifying affected individuals in a timely manner. By proactively addressing security vulnerabilities and responding swiftly to incidents, organisations can uphold the trust and confidence of their customers and stakeholders.
Tools and technologies for PII protection
Advancements in technology have given rise to a variety of tools and solutions designed to enhance the protection of Personally Identifiable Information (PII) and strengthen data privacy practices. Data loss prevention (DLP) software, for instance, helps organisations monitor and control the movement of sensitive data across networks, endpoints, and cloud applications, reducing the risk of data leakage or unauthorised access.
Data Security Posture Management solutions are an enhancement to DLP, as well as mapping and classifying data they allow you to automate remediations efforts (controls, consents, Notifiable Data Breach Reporting (NDBR), ROPA) and reduce organisation liability by over exposure of data and holding data beyond its sell by date (retention periods).
Identity and access management (IAM) platforms provide centralised control over user permissions and authentication, allowing organisations to manage user identities, access levels, and privileges effectively. By implementing IAM solutions, businesses can enforce strong authentication practices, streamline user provisioning processes, and monitor user activity to detect suspicious behaviour.
Additionally, encryption tools, secure file sharing platforms, and anonymisation techniques offer further layers of protection for PII, ensuring that data remains confidential and secure both in transit and at rest. By leveraging these tools in conjunction with best practices and security controls, organisations can fortify their data protection strategies and minimise the risk of data breaches and privacy incidents.
As the cybersecurity landscape continues to evolve, staying informed about the latest tools and technologies for PII protection is essential for maintaining a strong security posture and adapting to emerging threats. By investing in the right solutions and staying proactive in their approach to data privacy, organisations can uphold the confidentiality and integrity of personal information in an increasingly connected world.
Conclusion: Taking control of your PII
In todays threat landscape where personal information is constantly at risk, taking control of your Personally Identifiable Information (PII) is paramount in safeguarding your privacy and security. By understanding what constitutes PII, the risks associated with its exposure, and the best practices for protecting it, organisations can empower themselves to make informed decisions about how they handle, share and protect data.
From implementing encryption and access controls to staying informed about data protection regulations and leveraging privacy-enhancing technologies, there are numerous steps individuals can take to enhance the security of their PII. By remaining vigilant, practising good cyber hygiene, and being mindful of the information they disclose online, individuals can reduce their exposure to identity theft, fraud, and other privacy risks.
Ultimately, the responsibility for protecting PII extends beyond individuals to organisations, governments, and technology providers. By working together to promote data privacy and security, we can create a safer and more trustworthy digital ecosystem where personal information is respected, protected, and used responsibly. Hopefully by prioritising privacy and taking proactive steps to safeguard our PII, we can build a more secure and resilient digital future for generations to come.
For further information and a complimentary guide to Data Privacy, download our Data Security and Privacy Solutions Guide.