Posts by John Reeman
Data Security in the era of AI
In the era of AI, forward-thinking organisations need to adopt a new approach to protecting their most sensitive data.
The growing volume of data and the propensity of its use means that organisations can no longer rely on traditional and manual data processing methods to manage unstructured data. The only way to manage data in the future will be with automation, and ironically AI.
Read MoreCyberChef : how to decode your data the easy way
Intro If you haven’t heard of CyberChef you may be thinking that it is a new robot being created to compete on the next series of “My Kitchen Rules” or go head to head with Gordon Ramsay on “Kitchen Nightmares”! Actually CyberChef or at least the one I’m referring to is actually a really cool…
Read MoreHow to build and maintain a successful cybersecurity program
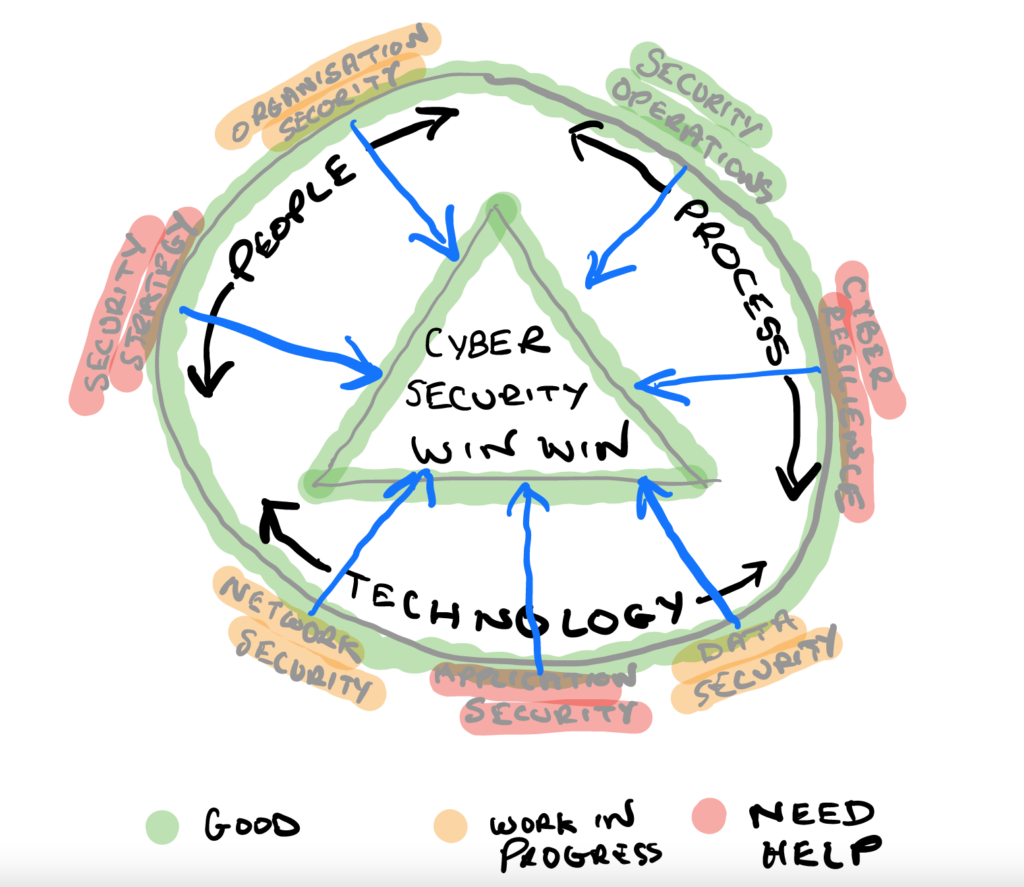
In this article I’m going to be talking about how to build a successful cybersecurity program. This unique strategy is something I’ve learned and put into action over the last 30 years and that has helped to keep organisations safe, build resilience and maintain a continuous improvement plan that provides a WIN WIN for cybersecurity…
Read MoreHow to measure the success of your cybersecurity program
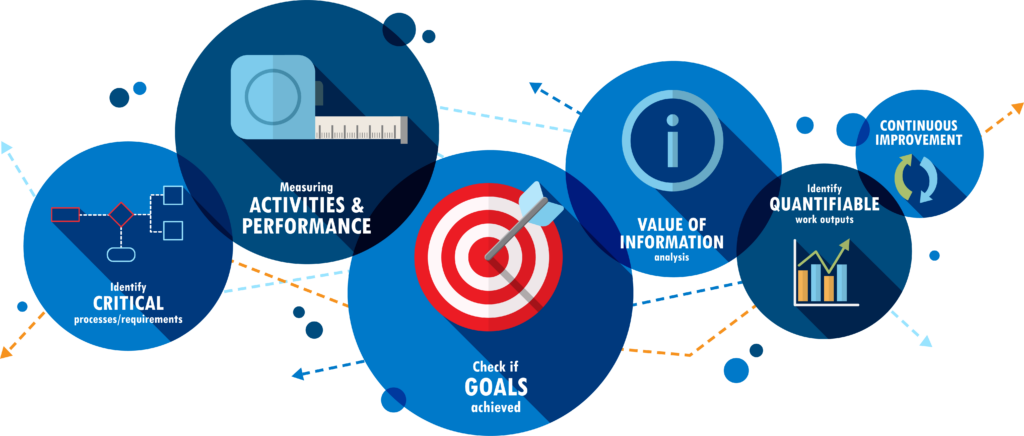
Being asked to present to the board and other key stakeholders in your business about the state of your cybersecurity program can be a daunting prospect.
Putting aside the technical jargon can also be challenging for even the most seasoned security professional.
Read MoreRansomware Resilience: How to prepare and respond in a crisis
Are you prepared for a ransomware attack? What should you do if you become a victim? This guide provides some practical advice you need to know & do to survive.
Read MoreTime altering techniques to evade your security controls
In this article I’ll be talking about ‘Time Travel’ and sadly it’s not an episode of ‘Dr Who’ or ‘Back to the Future’ and not really ‘Time Travel’ but I needed a catchy title! So what I am referring to is how hackers often change the system time of a particular system they are exploiting…
Read MoreEndpoint Security Part 5: How to setup an automated isolation workflow when malware is detected
In this continuing series on endpoint security protections I’ll be showing you how to fully automate host isolation using ‘Tines’ and ‘Elastic’. This article assumes you are familiar with using Elastic SIEM and have some exposure to Tines. Tines is a smart automation workflow solution that I came across last year. What I like about…
Read MoreEndpoint Security Part 4: How to create a playbook to isolate a machine and alert your SOC team
Overview In this fourth article of a 5 part series on ‘Endpoint Security’ I’m going to be showing you how to create a rule in your Elastic SIEM to generate an alert and isolate a host if the presence of malware is detected. Step One – Create the detection rule In your Kibana console select:…
Read MoreFidelity National Financial acknowledges data breach affecting 1.3 million customers
Fidelity National Financial has suffered a ransomware attack and resulting data breach which involved 1.3 million of its customers’ data.
Read MoreEndpoint Security Part 3: How to correlate threat intelligence
Overview In this third article of a 5 part series on ‘Endpoint Security’ I’m going to be showing you how you can incorporate ‘Threat Intelligence’ into your security operations strategy. There has been a lot written about threat intelligence over the last decade and it has different meanings to people depending on what industry you…
Read More